Cairo ICT CTF 2022 by Cyshield
My write-ups to many challenges in Cairo ICT CTF 2022 by Cyshield

In this CTF competition, we got 11th place after great work and speed in solving challenges
My write-ups to many challenges in Cairo ICT CTF 2022 by Cyshield


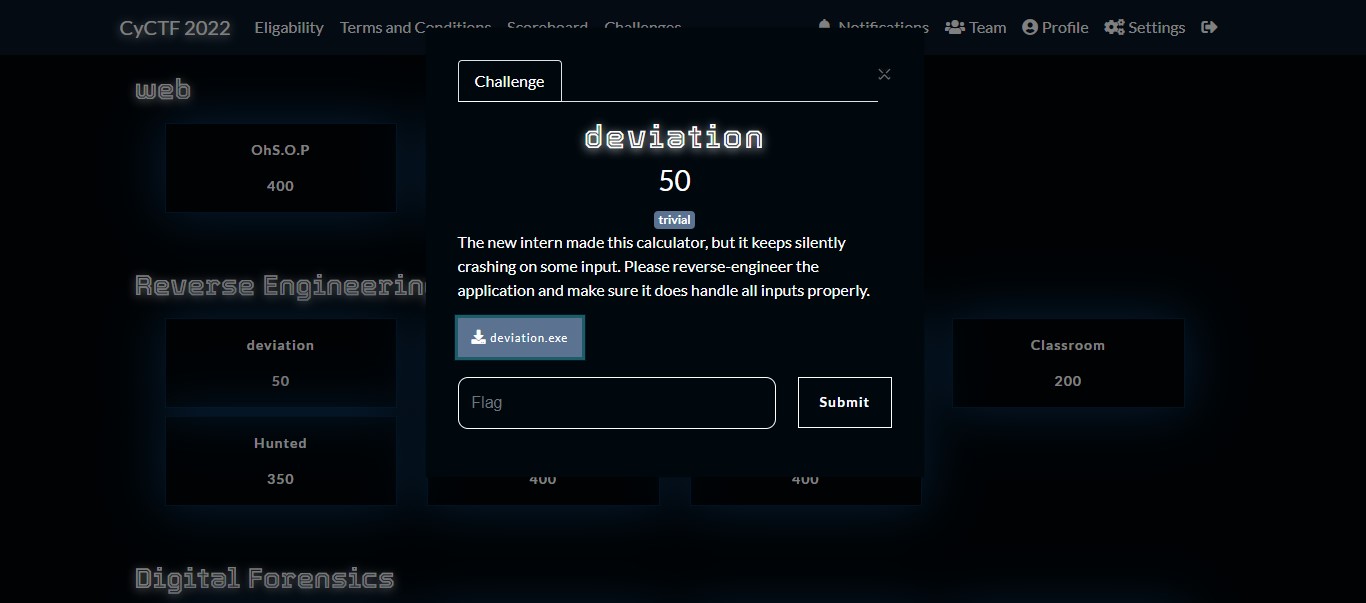

https://fileinfo.com/extension/ll
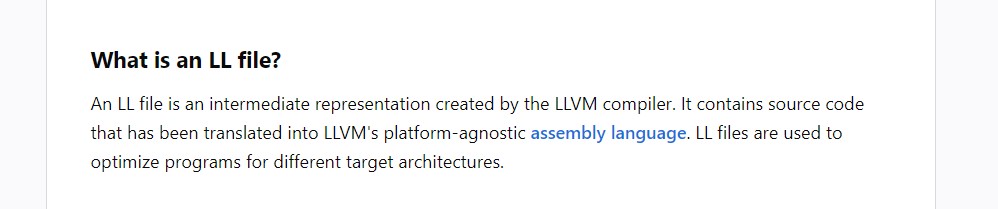
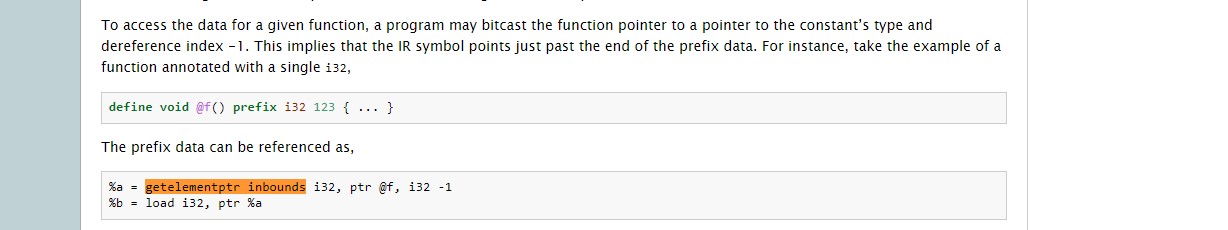
https://llvm.org/docs/LangRef.html
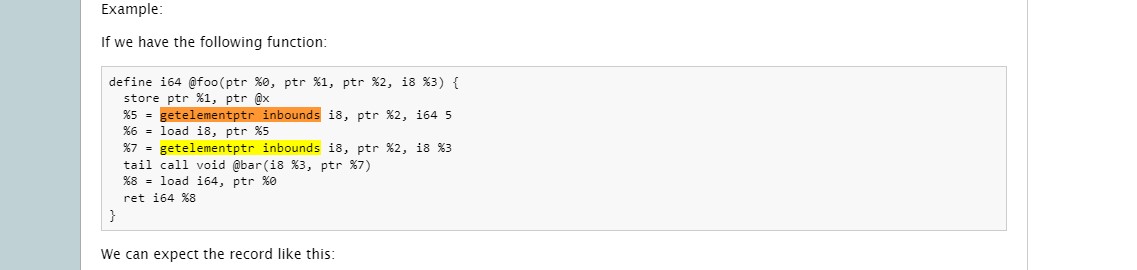
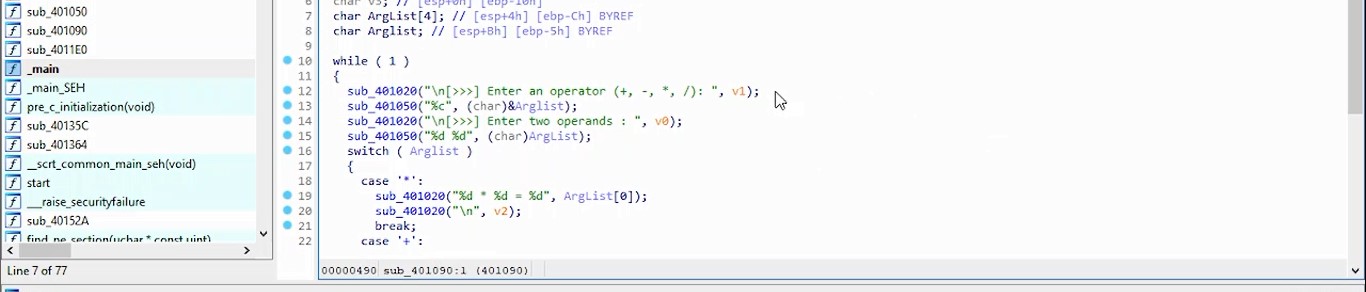
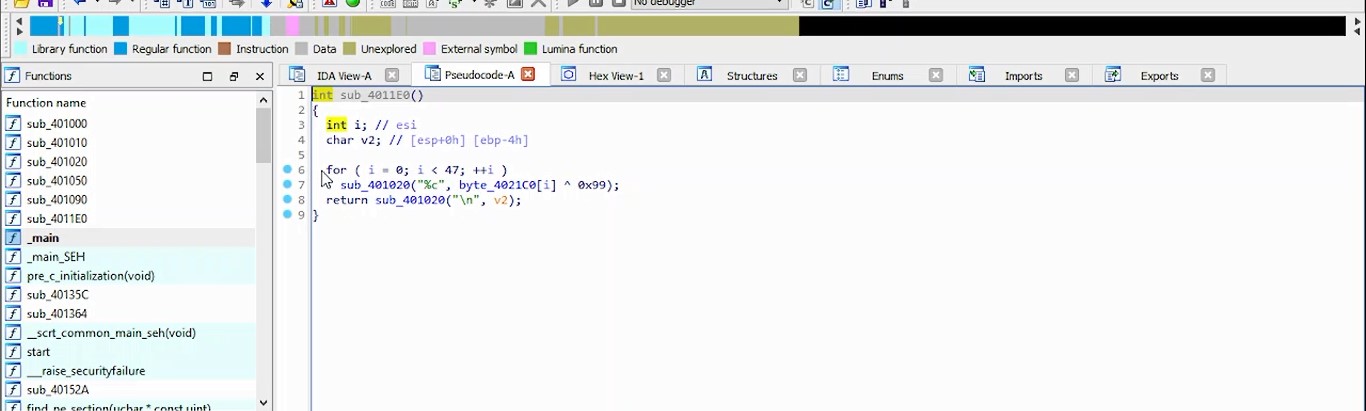
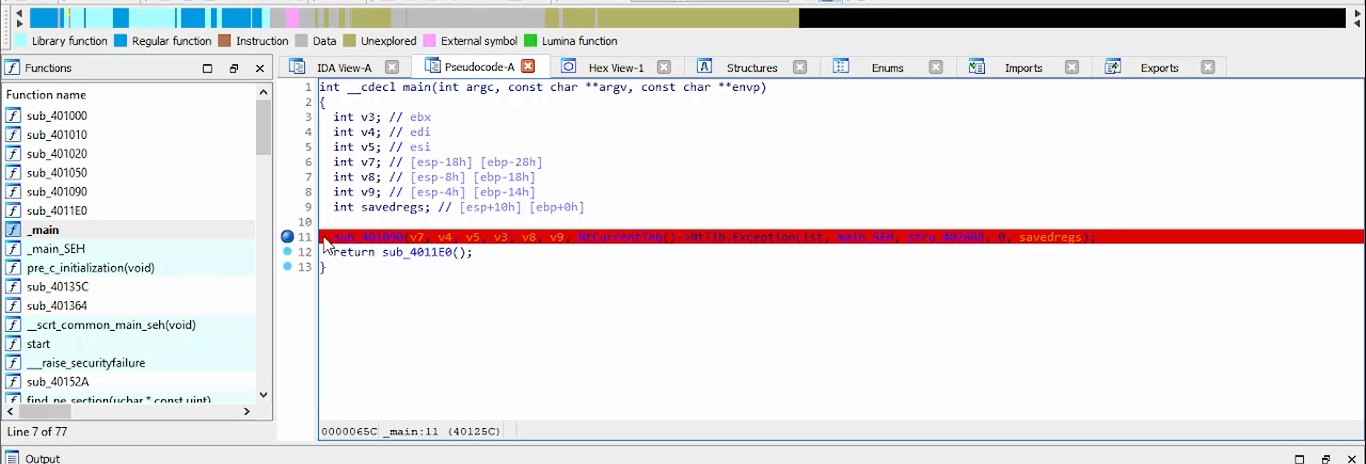
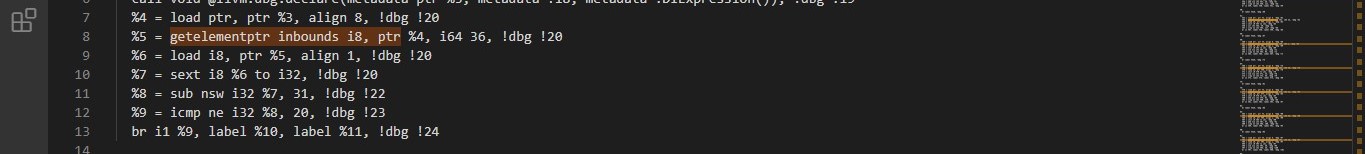
%4 = load ptr, ptr %3, align 8, !dbg !20%5 = getelementptr inbounds i8, ptr %4, i64 36, !dbg !20%6 = load i8, ptr %5, align 1, !dbg !20%7 = sext i8 %6 to i32, !dbg !20%8 = sub nsw i32 %7, 31, !dbg !22%9 = icmp ne i32 %8, 20, !dbg !23br i1 %9, label %10, label %11, !dbg !24x[36]-31=20 which mean
x[36]=51 which equal to "3" from ascii
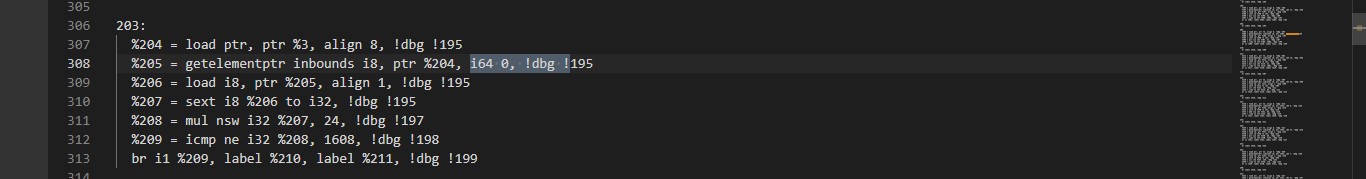
x[0]*24=1608 which mean x[0]=67 which equal to
"C" from ascii
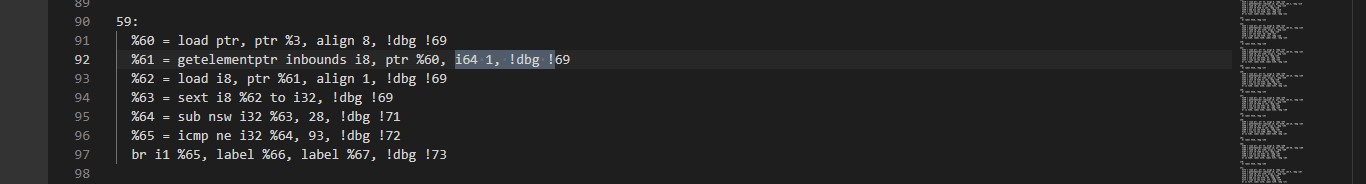
x[1]-28=93 which mean x[1]=121 which equal to
"y" from ascii
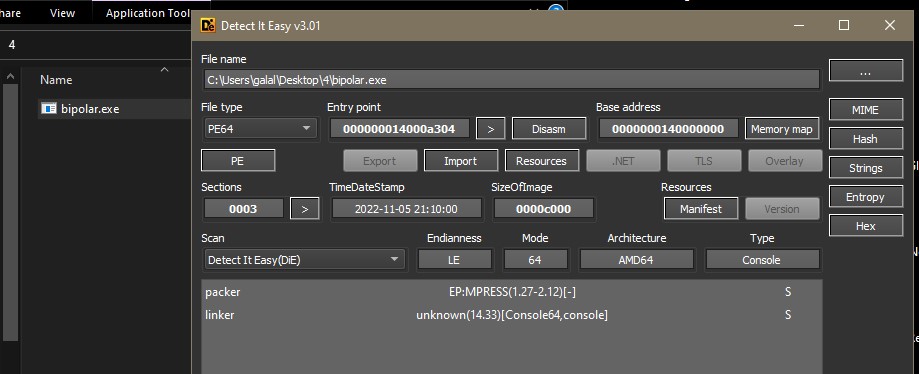
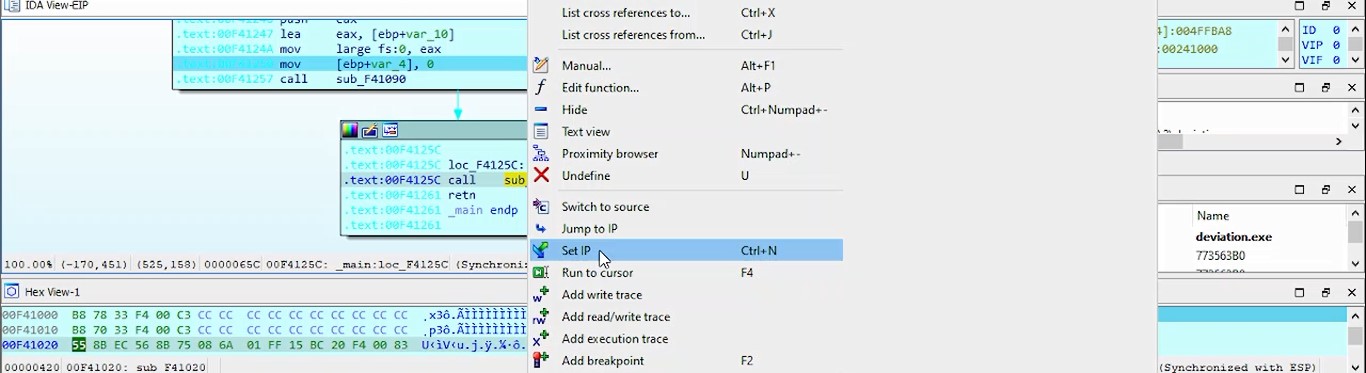
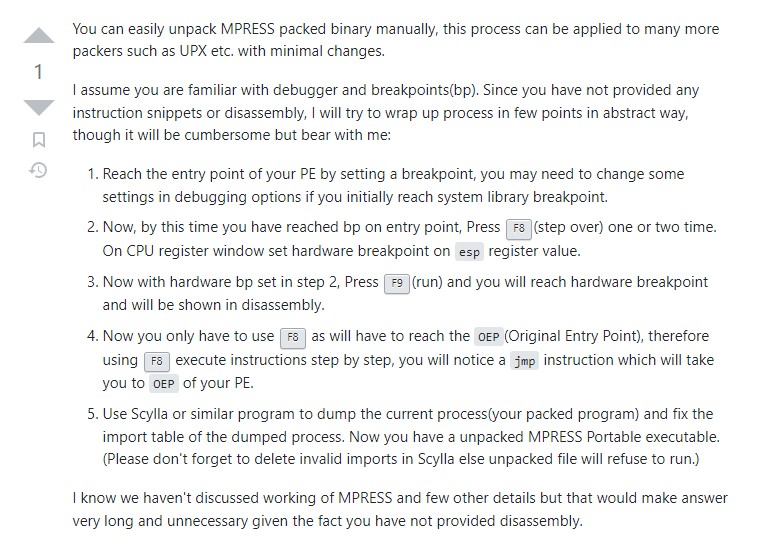
https://reverseengineering.stackexchange.com/questions/30545/how-do-i-unpack-a-file-protected-by-mpress
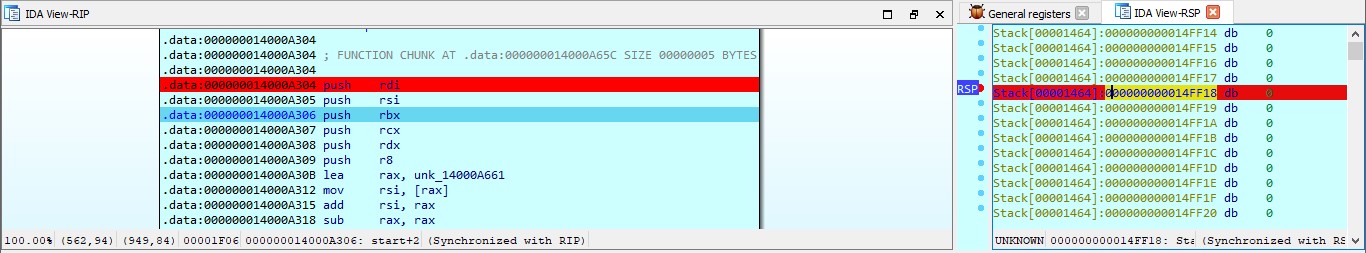
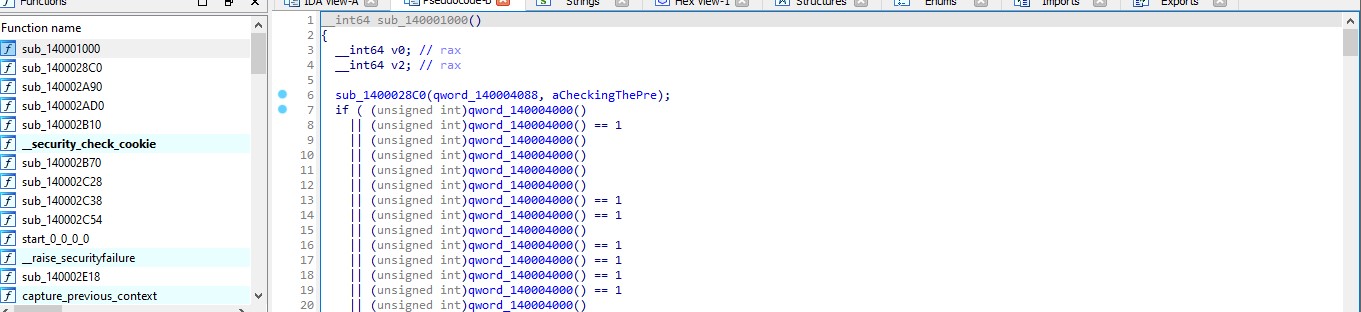
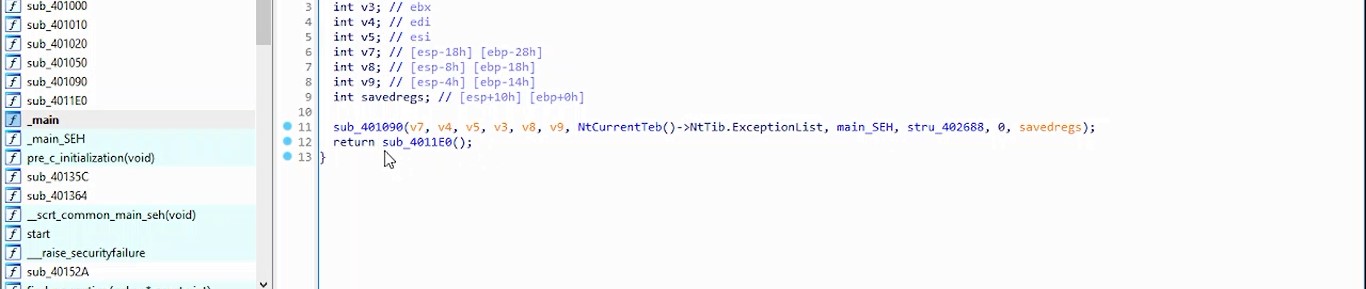
sub_140001000
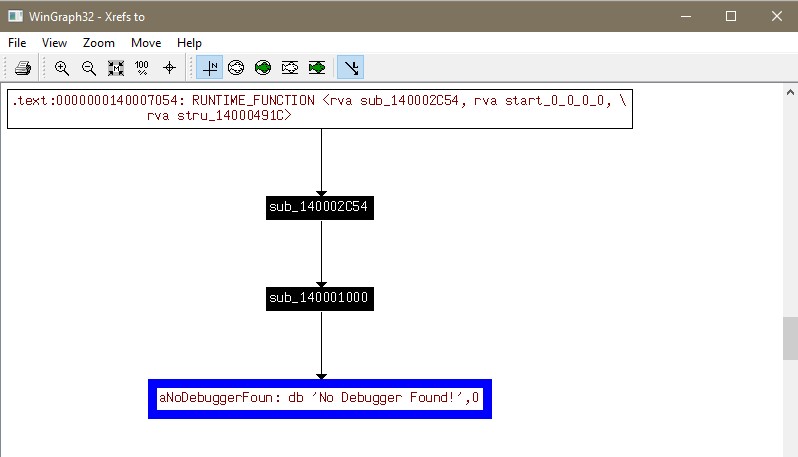
sub_140001000 i found that :