CAT Reloaded CTF 2023 by 0xL4ugh
My write-ups to My reverse challenges in CAT Reloaded CTF 2023

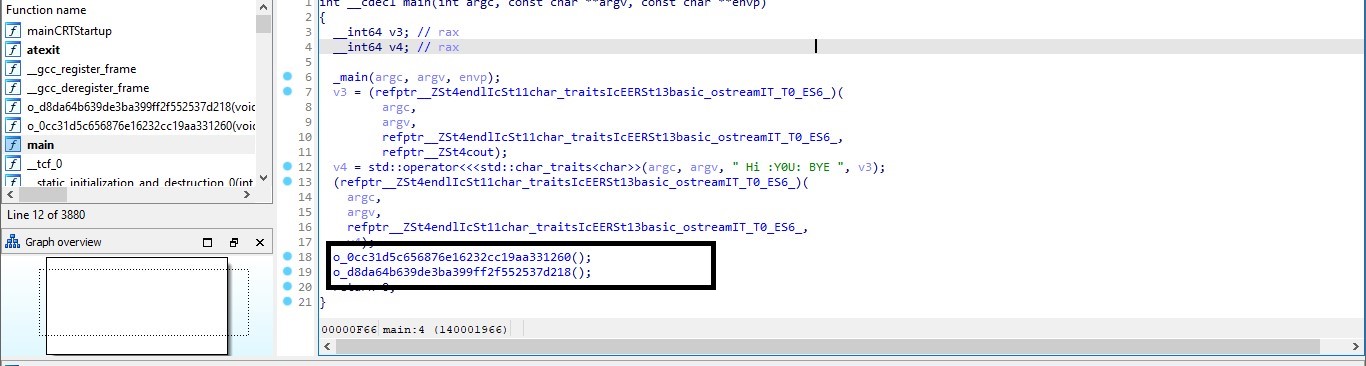
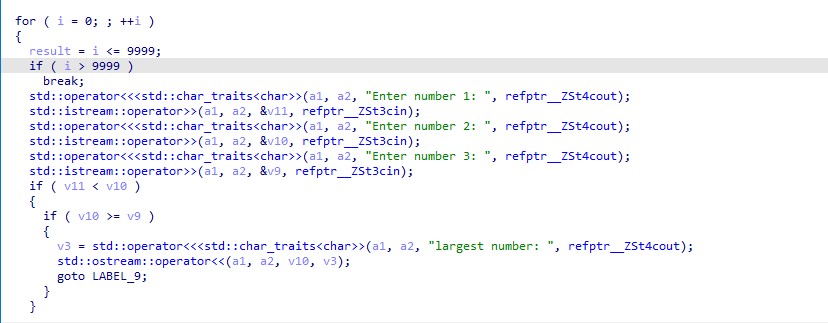
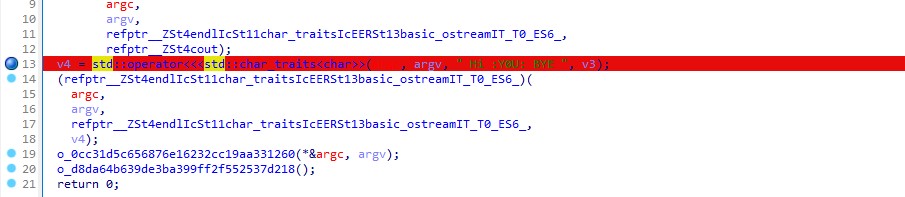
During the CTF competition, I had the opportunity to author two reverse challenges and thoroughly enjoyed the process. Not only was it a fun experience, but it also provided me with valuable knowledge and expertise in reverse engineering field . I hope that my friends who participated in the competition also enjoyed solving these challenges and gained new skills as well. Overall, being a part of this competition was a rewarding experience that allowed me to grow and learn in my field.
- Name Category Level
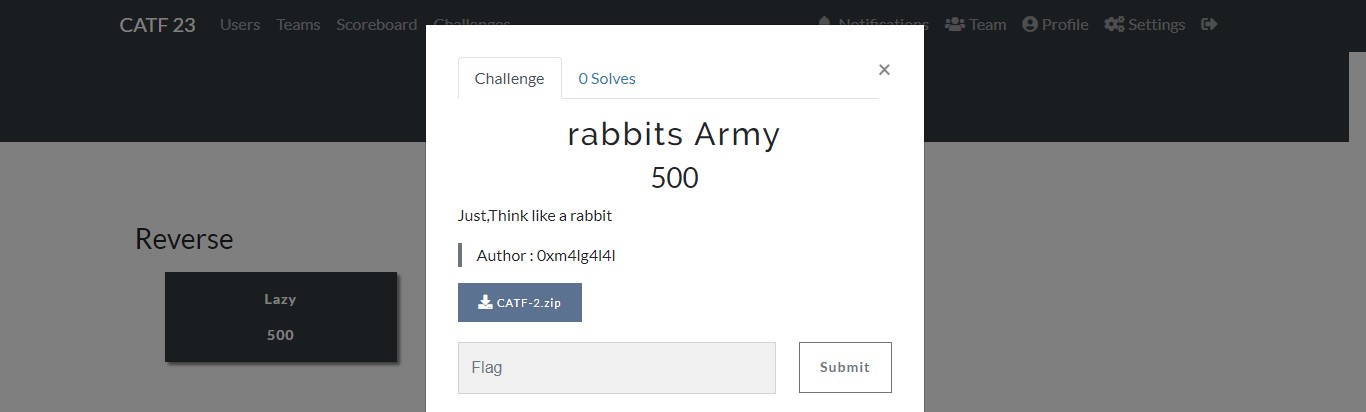
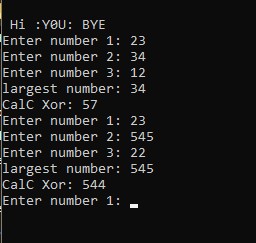
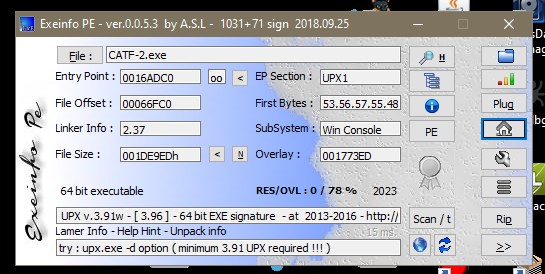
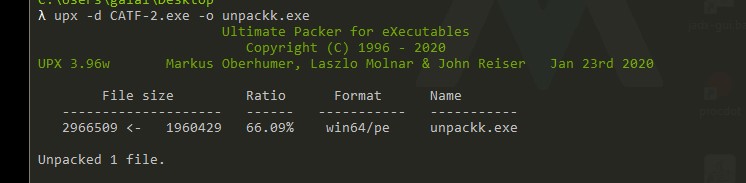
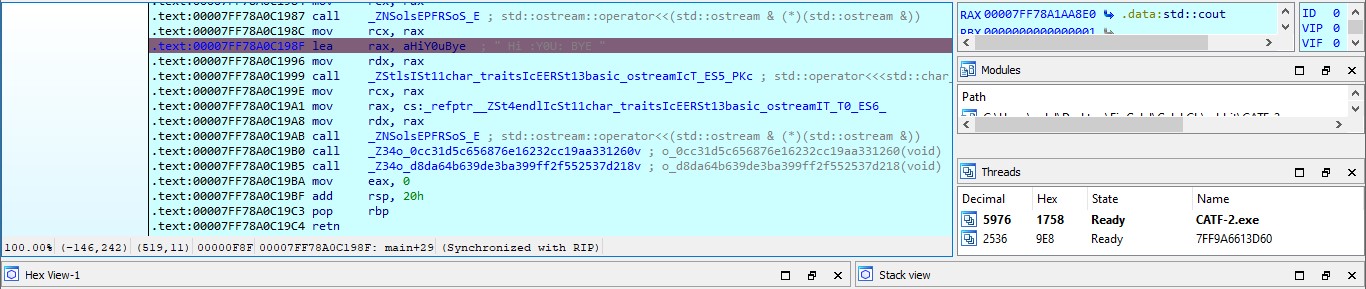
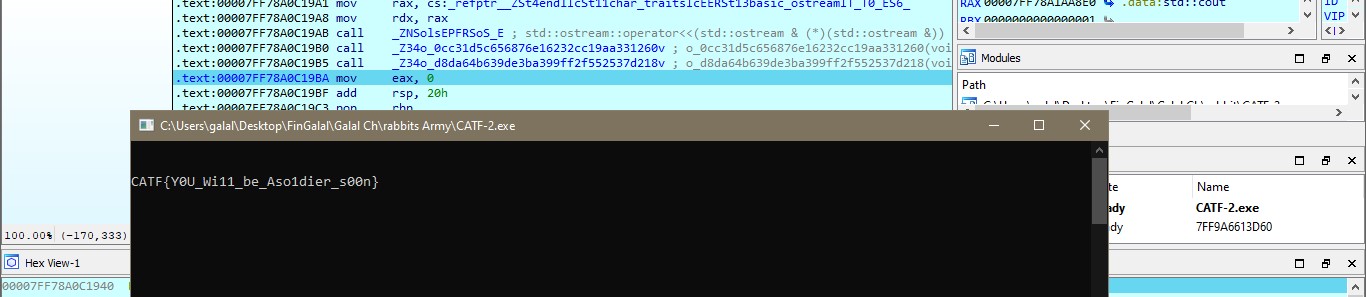
- rabbits Army Reverse Medium
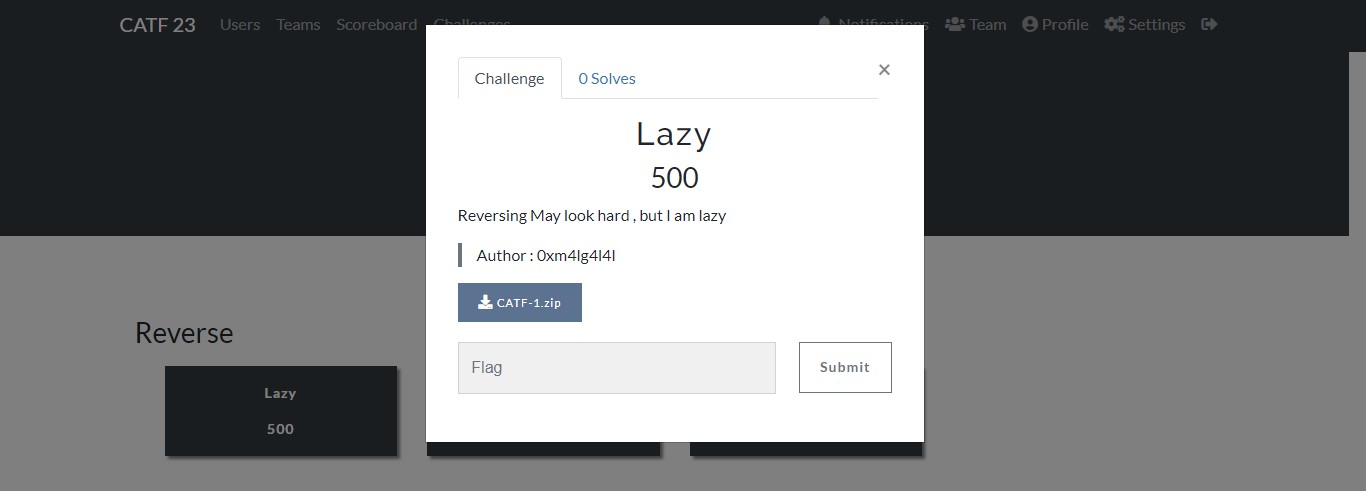
- Lazy Reverse Medium